Here at the Hackaday we’ve been enjoying a peculiar side effect of the single-port USB-C world; the increasing availability of programmable DC power supplies in the form of ubiquitous laptop charging bricks. Once the sole domain of barrel jacks or strange rectangular plugs (we’re looking at you Lenovo) it’s become quite common to provide charging via the lingua franca of USB-C Power Delivery. But harnessing those delectable 100W power supplies is all to often the domain of the custom PCBA and firmware hack. What of the power-hungry hacker who wants to integrate Power Delivery in her project? For that we turn to an excellent video by [Brian Lough] describing four common controller ICs and why you might choose one for your next project.
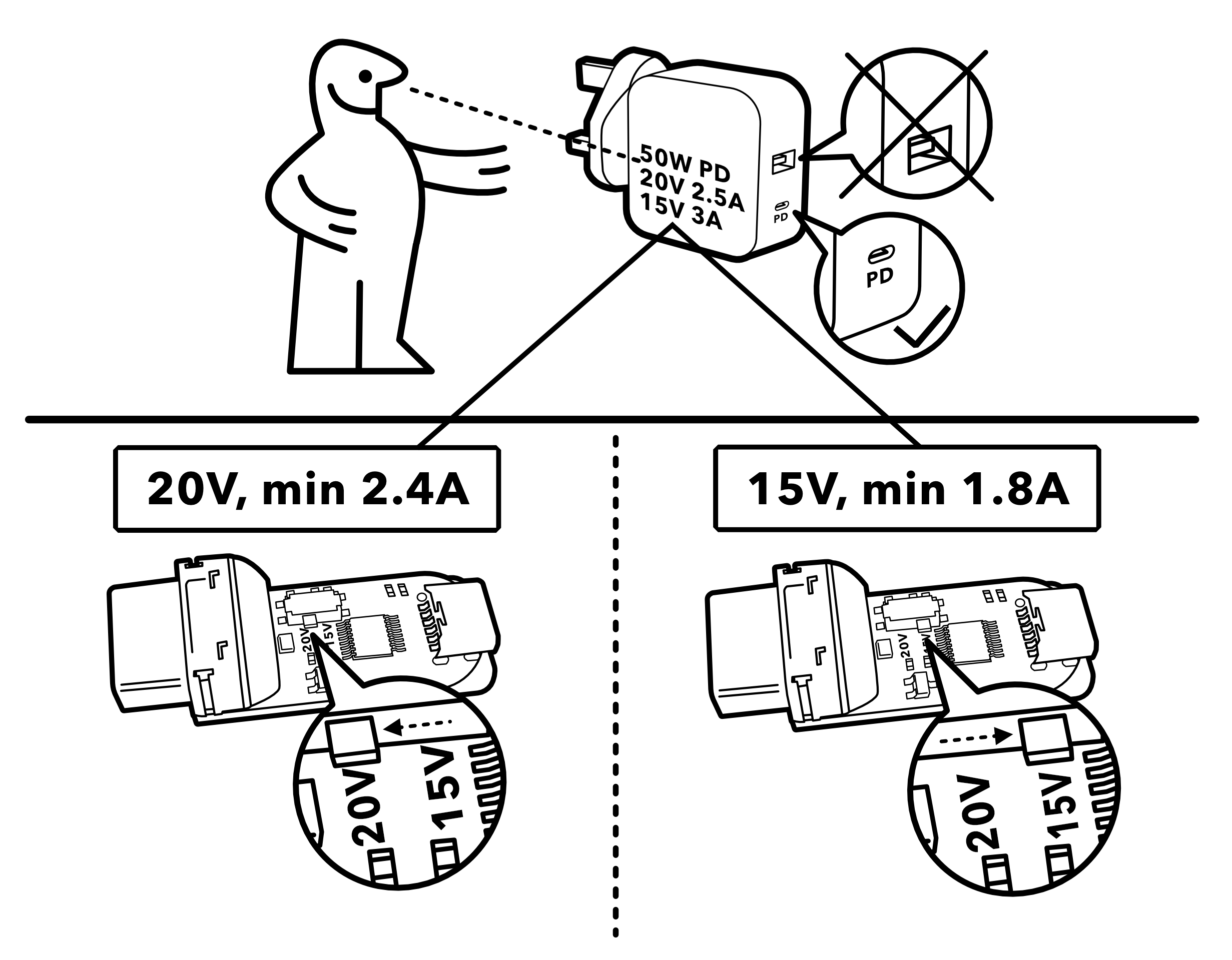
[Brian] starts off with a sorely-needed explainer of what the heck Power Delivery is; a topic with an unfortunate amount of depth. But the main goal of the video is to dive into the inscrutable hoard of “USB C trigger boards.” Typically these take USB on one side and provide a terminal block on the other, possibly with a button or LED as user interface to select voltage and current. We’ve seen these before as laptop barrel jack replacements and TS100 power supplies but it’s hard to tell which of the seemingly-identical selection is most suitable for a project.
The main body of the video is [Brian’s] detailed walkthrough of four types of trigger boards, based on the IP2721, FUSB302, STUSB4500, and Cypress EZ-PD BCR. For each he describes the behaviors of it’s particular IC and how to configure it. His focus is on building a board to power a TS100 (which parallels his TS100 Flex-C-Friend) but the content is generally applicable. Of course we also appreciate his overview of the products on Tindie for each described module.
For another angle on Power Delivery, check out this series of posts by [jason cerudolo], a perennial favorite. And don’t miss his classic project, the USB Easy Bake Oven.

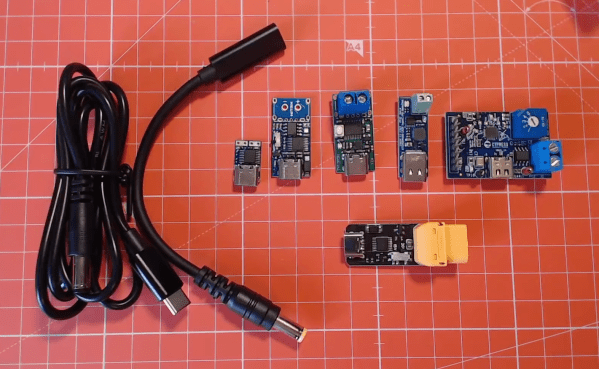

 Each module is composed a very boring PCBA base layer which should be inexpensive from the usual sources, even when ordering one
Each module is composed a very boring PCBA base layer which should be inexpensive from the usual sources, even when ordering one