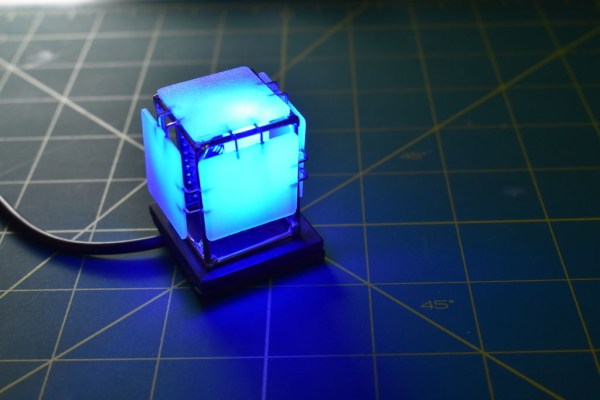
If you’re planning to get into circuit sculpture one of these days, it would probably be best to start with something small and simple, instead of trying to make a crazy light-up spaceship or something with a lot of curves on the first go. A small form factor doesn’t necessarily mean it can’t also be useful. Why not start by making a small automatic night light?
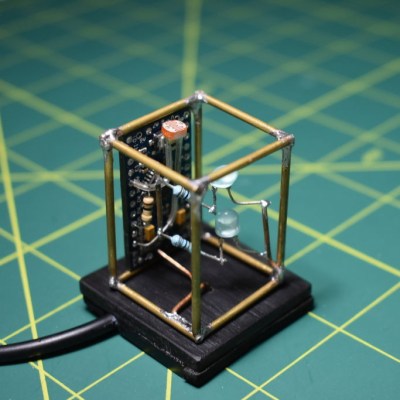 The circuit itself is quite simple, especially because it uses an Arduino. You could accomplish the same thing with a 555, but that’s going to complicate the circuit sculpture part of things a bit. As long as the ambient light level coming in from the light-dependent resistor is low enough, then the two LEDs will be lit.
The circuit itself is quite simple, especially because it uses an Arduino. You could accomplish the same thing with a 555, but that’s going to complicate the circuit sculpture part of things a bit. As long as the ambient light level coming in from the light-dependent resistor is low enough, then the two LEDs will be lit.
We love the frosted acrylic panels that [akshar1101] connected together with what looks like right angle header pins. If you wanted to expose the electronics, localize the light diffusion with a little acrylic cover that slips over the LEDs. Check it out in the demo after the break.
There’s more than one way to build a glowing cuboid night light. The Rubik’s way, for instance.
Continue reading “Tiny Circuit Sculpture Keeps The Night Watch”