[Dave Madison] came across some old digital photos, and in his quest to access them, he ran into quite a few challenges. The saga brings to mind both Murphy’s Law, and while [Dave] prevailed in the end, it required quite a few more steps than one might expect.
Here’s the scene: in the late 90s, Konica partnered with photo shops to provide a photo scanning service, delivering digital scans of film photos on 3.5″ floppy disks, and that’s exactly what [Dave] had to work with. The disks were in good condition, and since modern desktop computers still support floppy drives and the FAT filesystem, in theory all one needs to do is stick disks into the reader one at a time in order to access the photos.
Sadly, problems started early. A floppy drive is revoltingly slow compared to any modern storage device, so [Dave]’s first step was to copy all of the files to his machine’s local storage before working on them. This took a bit of wrangling to deal with 8.3 format file names and avoid naming collisions across disks while still preserving some metadata such as original creation date. It was nothing a quick python script couldn’t handle, but that soon led to the next hurdle.
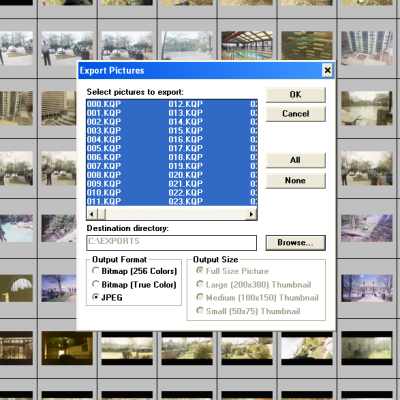
The photos in question were in an obsolete and proprietary Konica .KQP format. [Dave] went through a number of photo viewing programs that claimed to support .KQP, but none of them actually recognized the images.
Fortunately, each disk contained a copy of Konica’s proprietary “PC PictureShow” viewer, but despite having a variety of versions dated between 1997 and 2001 (making them from the Windows 98 and Windows ME eras) [Dave] could not get any version of the program to run in Windows 10, even with compatibility mode for legacy programs enabled. The solution was to set up a Windows XP virtual machine using Oracle’s Virtualbox, and use that to ultimately run PC PictureShow and finally access the photos. After all that work, [Dave] finally had a stroke of luck: Konica’s software had a handy feature to export images in JPEG format, and it worked like a charm.
In the end, [Dave] was able to save 479 out of the 483 images on the old floppy disks, with a reminder that proprietary formats are a pain. The disks and images may have been over twenty years old, but the roots of digital imaging go considerably further back than that. Take a few minutes out your day to read a bit about Russell Kirsch and the first digitized image, that of his three-month old son in 1957.