The good thing about listening in on satellites is that they tend to beam down all kinds of juicy information from their lofty perches. The bad thing about satellites is that to stay in those orbits, they’ve got to be moving really fast, and that means that you’ve got to track them if you want to keep a nice consistent signal during a pass. And that can lead to all sorts of complexity, with motorized two-axis mounts and fancy tracking software.
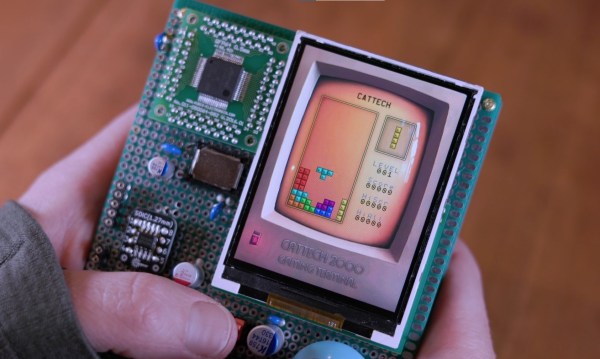
Or does it? Not if you’re willing to act as the antenna mount, which is the boat [Gabe] from the saveitforparts channel on YouTube recently found himself in when searching for L-band signals from the GOES satellite. His GOES setup uses a 30″ (0.8 m) dish repurposed from a long-range wireless networking rig. Unfortunately, the old security camera pan-tilt unit it was mounted on wasn’t quite up to satellite tracking duty, so [Gabe] pulled the dish off and converted it to manual tracking.
With a freshly wound helical antenna and a SAWbird LNA at the focal point, the dish proved to be pretty easy to keep on track manually, while providing quite the isometric workout. Aiming was aided by an app called Stellarium which uses augmented reality to point out objects in the night sky, and a cheap tablet computer was tasked with running SDR++ and capturing data. Sadly, neither of these additions brought much to the party, with the latter quickly breaking and the former geared more toward stargazing than satellite snooping. But with some patience — and some upper-body strength — [Gabe] was able to track GOES well enough with the all-in-one “cyberdish” to get some usable images. The whole saga is documented in the video after the break.
Kudos to [Gabe] for showing us what can be accomplished with a little bit of junk and a lot of sticktoitiveness. He promises that a legit two-axis mount is in the works, so we’ll be on the lookout for that. We’ve seen a few of those before, and [Chris Lott] did a great overview of satellite tracking gear a while back, too.
Continue reading “Junk Bin Cyberdish Turns You Into The Satellite Tracker”




![Automated hydrogen generator setup, courtesy of [Hyperspace Pirate]'s dog drinking bowl.](https://hackaday.com/wp-content/uploads/2023/10/automated_hydrogen_generator_basics.jpg?w=400)