For the last few years of the Hackaday Prize, we’ve seen a few projects that aim to bring Braille to the masses in a cheap, easy to use electronic device. Aside from the interesting technology that would go into such a device like tiny motors moving even tinier bumps, these projects are a great example of an enabling technology.
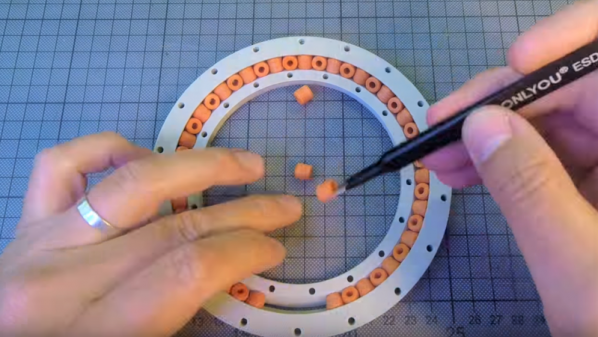
For his Hackaday Prize project, [haydn jones] is building something that makes Braille more accessible, but without all that messy technology. It’s 3D printed movable type for Braille. It’s a Braille printing press for nurses, teachers, and anyone else who would like to leave small notes for people who read Braille.
This Hackaday Prize project is the answer to the question, ‘how do you leave a note for a blind person’. Yes, digital voice recorders exist, but movable type is a technology that’s thousands of years old and doesn’t require batteries or any of the other failings of modern electronics. To use this device, all you need to do is assemble a message — a handy Braille cheat sheet is coming soon — and emboss a piece of paper. Keep in mind Braille embossers cost a small fortune, and this project is simple and cheap bits of plastic.
It’s a great idea, and one we’re surprised we haven’t seen before. All in all, a great entry for The Hackaday Prize.