If your favourite programming language is solder, they you’ve surely worked your way through a bunch of irons and controllers over your hacker existence. It’s also likely you couldn’t pick one single favourite and ended up with a bunch of them crowding your desk. It would be handy to have one controller to rule them all. That’s just what [sparkybg] set out to do by building his Really Universal Soldering Controller. His intent was to design a controller capable of driving any kind of low voltage soldering iron which used either an in-line or separate temperature sensor (either thermocouple or resistive PTC).
 This project has really caught on. [sparkybg] announced his build about two years back and since then many others have started posting details of their own Unisolder 5.2 builds. [zed65] built the version seen to the right and [SZ64] assembled the boards shown at the top of this article.
This project has really caught on. [sparkybg] announced his build about two years back and since then many others have started posting details of their own Unisolder 5.2 builds. [zed65] built the version seen to the right and [SZ64] assembled the boards shown at the top of this article.
The controller has been proven to work successfully with Iron handles from Hakko, Pace, JBC, Weller, Ersa, as well as several Chinese makes. Getting the controller to identify one of the supported 625 types of iron profiles consists of connecting two close tolerance resistors across the relevant pins on the 9-pin shell connector. This is a brilliant solution to help identify a large variety of different types of irons with simple hardware. In the unlikely situation where you have a really vague, unsupported model, then creating your own custom profile is quite straightforward. The design is highly discrete with an all analog front end and a PIC32 doing all the digital heavy lifting.
To get an idea of the complexity of his task, here is what [sparkybg] needs to do:
“I have around 200 microseconds to stop the power, wait for the TC voltage to come to its real value, connect the amplifier to this voltage, wait for the amplifier to set its output to what I want to read, take the measurement from the ADC, disconnect the amplifier from the TC, run the PID, and eventually turn the power back on. The millivolts to temperature calculation is done using polynomial with 10 members. It does this calculation using 32bit mantissa floating point numbers and completes it in around 20 microseconds. The whole wave shaping, temperature calculation, PID and so on is completed in around 50-60 microseconds. RMS current, voltage and power calculations are done in around 100 microseconds. All this is done between the half periods of the mains voltage, where the voltage is less than around 3 volts.”
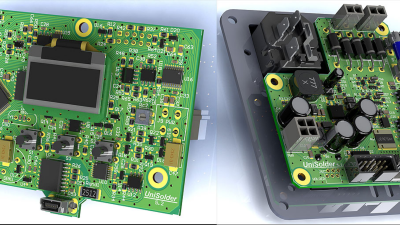
The forum is already over 800 posts deep, but you can start by grabbing the all important schematic PDF’s, Gerbers, BoM and firmware files conveniently linked in the first post to build your own Unisolder5.2 controller. This Universal Controller is a follow up to his earlier project for a Hakko T12/T15 specific controller which gave him a lot of insight in to designing the universal version.
[sparkybg] has posted several videos showing the UniSolder5.2 controlling several types of Irons. In the video after the break, he demonstrates it controlling a Weller WSP80.
Continue reading “One Soldering Controller To Rule Them All” →
 Our Hack Chats are live community events on the Hackaday.io Hack Chat group messaging.
Our Hack Chats are live community events on the Hackaday.io Hack Chat group messaging.




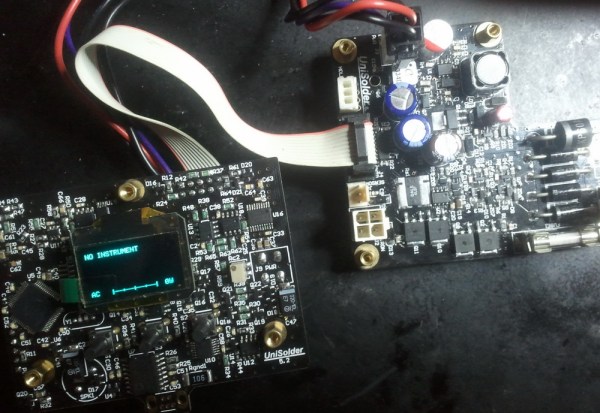
 This project has really caught on. [sparkybg] announced his build about two years back and since then many others have started posting details of their own Unisolder 5.2 builds. [zed65] built
This project has really caught on. [sparkybg] announced his build about two years back and since then many others have started posting details of their own Unisolder 5.2 builds. [zed65] built