In our ceaseless quest to bring you the best from the cheaper end of the global electronics markets, there are sometimes gadgets that we keep an eye on for a while because when they appear they’re just a little bit too pricey to consider cheap.
Today’s subject is just such a device, it’s a minimalist infra-red camera using the 8 pixel by 8 pixel Panasonic AMG8833 thermal sensor. This part has been around for a while, but even though any camera using it has orders of magnitude less performance than more accomplished models it has remained a little too expensive for a casual purchase. Indeed, these mini cameras were somewhere above £50 ($70) when they first came to our attention, but have now dropped to the point at which they can be found for somewhere over £30 ($42). Thirty quid is cheap enough for a punt on a thermal camera, so off went the order to China and the expected grey parcel duly arrived.
It’s a little unit, 40 mm x 35 mm x 18 mm, constructed of two laser-cut pieces of black plastic held together by brass stand-offs that hold a PCB between them, and on the front is a cut-out for the sensor while on the rear is one for the 35mm OLED display.At the side on the PCB is a micro USB socket which serves only as a power supply. It’s fair to say that this is a tiny unit.
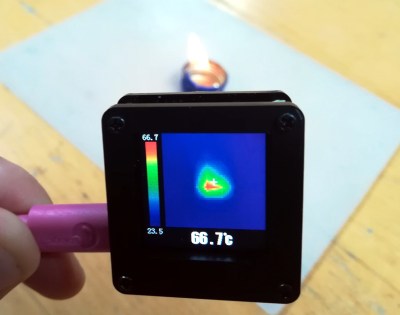
Applying power from a USB battery bank, the screen comes up with a square colour thermal picture and a colour to temperature calibration stripe to its left. The colours adapt to the range of temperatures visible to the sensor, and there is a crosshair in the centre of the picture for which the temperature in Celsius is displayed below the picture. It’s a very straightforward and intuitive interface that requires no instruction, which is handy because the device has none. Continue reading “Review: Mini AMG8833 Thermal Camera”