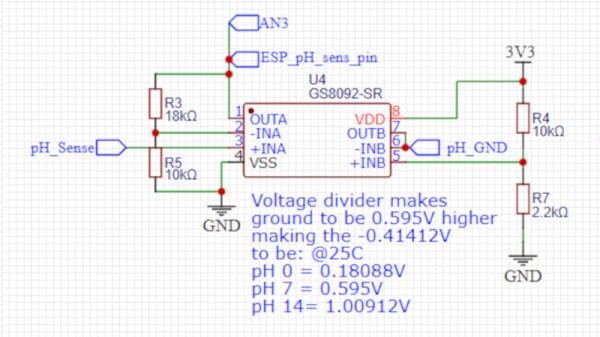
If you’re like us, one of the appeals of retro tech is the tactile feedback you get from real buttons. Researchers at Carnegie Mellon have developed a new method for bringing haptic feedback to touchscreen devices.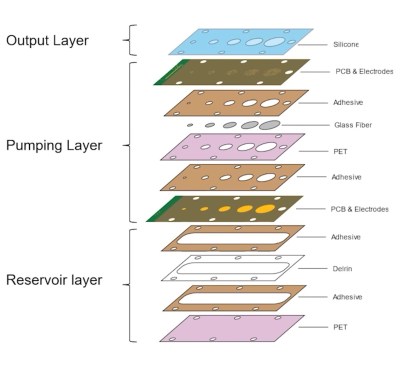
Using an array of miniaturized electroosmotic pumps, the current prototype devices offer 5 mm of displacement from a 5 mm stackup which is a significant improvement over previous technologies which required a lot more hardware than the displacement provided. When placed under a flexible screen, notifications and other user interactions like the keyboard can raise and lower as desired.
Each layer is processed by laser before assembly and the finished device is self-contained, needing only electrical connections. No need for a series of tubes carrying fluid to make it work. Interaction surfaces have been able to scale from 2-10 mm in diameter with the current work, but do appear to be fixed based on the video (below the break).
You might find applications for haptics in VR or want to build your own Haptic Smart Knob.
Continue reading “Electroosmotic Haptics For More Tactile Touch Devices”