Anyone with a cat knows that the little purring ball of fluff in your lap is one tiny step away from turning into a bloodthirsty serial killer. Give kitty half a chance and something small and defenseless is going to meet a slow, painful end. And your little killer is as likely as not to show off its handiwork by bringing home its victim – “Look what I did for you, human! Are you not proud?”
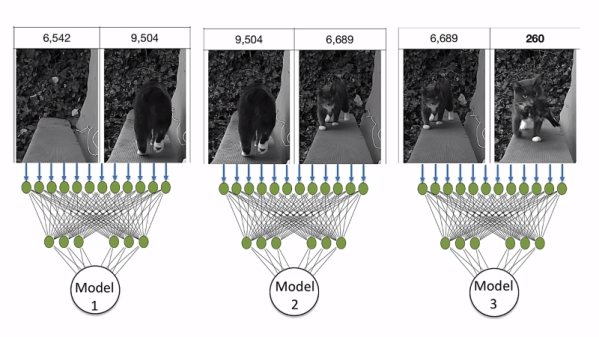
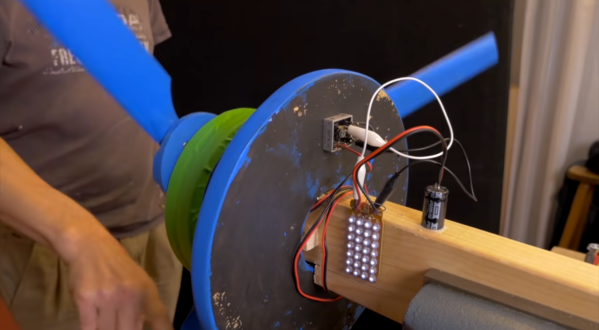
As useful as a murder-cat can be, dragging the bodies home for you to deal with can be – inconvenient. To thwart his adorable serial killer [Metric], Amazon engineer [Ben Hamm] turned to an AI system to lock his prey-laden cat out of the house. [Metric] comes and goes as he pleases through a cat flap, which thanks to a solenoid and an Arduino is now lockable. The decision to block entrance to [Metric] is based on an Amazon AWS DeepLens AI camera, which watches the approach to the cat flap. [Ben] trained three models: one to determine if [Metric] was in the scene, one to determine whether he’s coming or going, and one to see if he’s alone or accompanied by a lifeless friend, in which case he’s locked out for 15 minutes and an automatic donation is made to the Audubon Society – that last bit is pure genius. The video below is a brief but hilarious summary of the project for an audience in Seattle that really seems quite amused by the whole thing.
So your cat isn’t quite the murder fiend that [Metric] is? An RFID-based cat door might suit your needs better.




![An American-made Windsor chair from the turn of the 19th century. Los Angeles County Museum of Art [Public domain]](https://hackaday.com/wp-content/uploads/2019/05/Windsor_Arm_Chair_LACMA_54.80.jpg?w=280)












