One of the major advantages of OLED over LCD panels is that the former can be made using far fewer layers as the pixels themselves are emitting the light instead of manipulating the light from a backlight. This led some to ask the question of whether it’s possible to make an OLED panel that is transparent or at least translucent. As Xiaomi’s new Mi TV LUX OLED Transparent Edition shows, the answer there is a resounding ‘yes’. Better yet, for a low-low price of about $7,200 you can own one of these 55″ marvels.
Transparent OLED technology is not new, of course. Back in 2018 LG was showing off a prototype TV that used one of the early transparent OLED panels. In the video that is embedded after the break, [Linus] from Linus Tech Tips goes hands-on with that LG prototype while at LG in South Korea, while including a number of crucial details from an interview from one of the engineers behind that panel.
As it turns out, merely removing the opaque backing from an OLED panel isn’t enough to make it transparent. In order for an OLED panel to become transparent, the circuitry in the pixel layer and TFT layer need to be aligned as best as possible to allow for many, many tiny holes to be punched through the display.
Looking at [Linus]’s experiences with the LG prototype, it does appear that this kind of technology would be highly suitable for signage purposes, while also allowing for something like an invisible television or display in a room that could be placed in front of a painting or other decoration. Once displaying an image, the screen is bright enough that you can comfortably make out the image. Just don’t put any bright lights behind the TV.
Anyone else anxious waiting for sub-10″ versions of these panels?
Continue reading “Transparent OLED Hitting The Market With Xiaomi’s Mi TV LUX Transparent Edition”


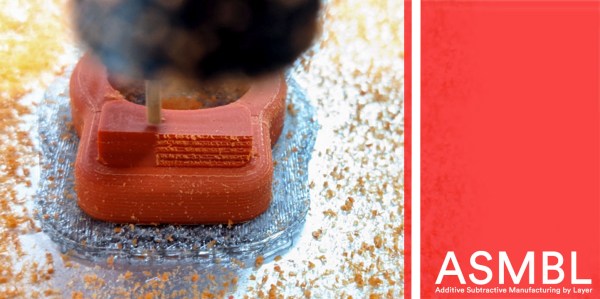
 Dubbed ASMBL (Additive/Subtractive Machining By Layer), the process is actually the merging of two complimentary processes combined into one workflow to produce a single part. Here, vanilla 3D printing does the work of producing the part’s overall shape. But at the end of every layer, an endmill enters the workspace and trims down the imperfections of the perimeter with a light finishing pass while local suction pulls away the debris. This concept of mixing og coarse and fine manufacturing processes to produce parts quickly is a re-imagining of a tried-and-true industrial process called near-net-shape manufacturing. However, unlike the industrial process, which happens across separate machines on a large manufacturing facility, E3D’s ASMBL takes place in a single machine that can change tools automatically. The result is that you can kick off a process and then wander back a few hours (and a few hundred tool changes) later to a finished part with machined tolerances.
Dubbed ASMBL (Additive/Subtractive Machining By Layer), the process is actually the merging of two complimentary processes combined into one workflow to produce a single part. Here, vanilla 3D printing does the work of producing the part’s overall shape. But at the end of every layer, an endmill enters the workspace and trims down the imperfections of the perimeter with a light finishing pass while local suction pulls away the debris. This concept of mixing og coarse and fine manufacturing processes to produce parts quickly is a re-imagining of a tried-and-true industrial process called near-net-shape manufacturing. However, unlike the industrial process, which happens across separate machines on a large manufacturing facility, E3D’s ASMBL takes place in a single machine that can change tools automatically. The result is that you can kick off a process and then wander back a few hours (and a few hundred tool changes) later to a finished part with machined tolerances.