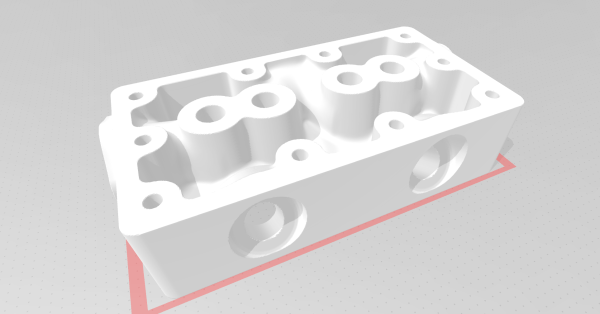
For those who model CAD models regularly, a pair of calipers is essential as it allows reasonably accurate measurements to fit a specific part. However, [Jason Harris] is taking that concept to the next level with a signed distance function-based CAD tool, SDFX.
For those who don’t know, Signed Distance Functions can tell you from a given point how close the nearest part of the model is. The model is represented as a single function that offers some exciting benefits. For instance, chamfering and fileting are often quite complex in traditional CAD programs and trivial in an SDF setting. SDFX is a golang library that allows you to write golang programs to describe the model. OpenSCAD is a favorite of Hackaday as it is a beautiful parametric code-first CAD package. But the syntax and language are somewhat cludgy, to say the best. The advantage of using golang rather than a DSL is that you can use all the niceties that a full-featured language brings. For example, you can export multiple objects, make network requests, and interface with GUI libraries to recreate something like the customizer for OpenSCAD.
Objects are rendered to STL using Marching squares. Then, they can be printed in whatever slicing software suits your fancy. It’s an excellent project with a great API and almost a hundred examples.
The code is available on GitHub under an MIT License.