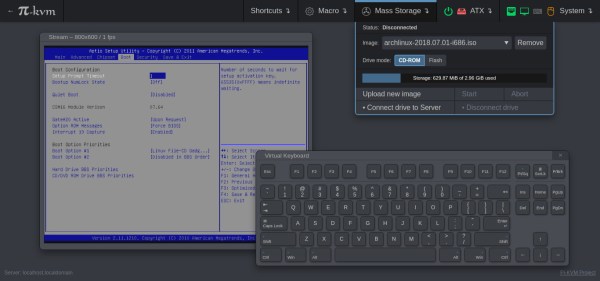
For administering many computers at once, an IP KVM is an invaluable piece of equipment that makes it possible to get the job done over the network without having to haul a keyboard, monitor, and mouse around to each computer. The only downside is that they can get pricey, unless of course you can roll one out based on the Raspberry Pi and the PiKVM image for little more than the cost of the Pi itself.
The video linked below shows how to set all of this up, which involves flashing the image and then setting up the necessary hardware. The build shows an option for using HDMI over USB, but another option using the CSI bus would allow for control over options like video resolution and color that a USB HDMI dongle doesn’t allow for. It also makes it possible to restart the computer and do things like configure BIOS or boot from removable media, which is something that would be impossible with a remote desktop solution like VNC.
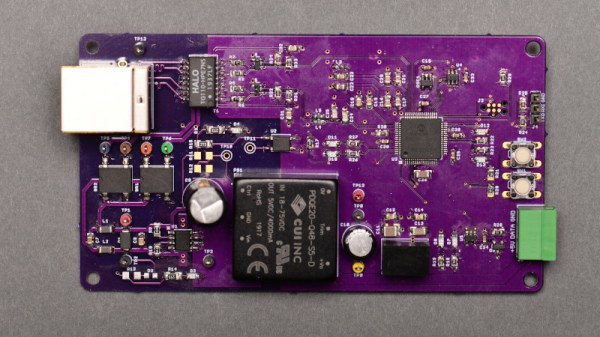
The creator of PiKVM was mentioned in a previous post about the creation of the CSI bus capture card, and a Pi hat based on this build will be available soon which would include options for ATX controls as well. Right now, though, it’s possible to build all of this on your own without the hat, and is part of what makes the Pi-KVM impressive, as well as its very low cost.
Continue reading “True Networked KVM Without Breaking The Bank”