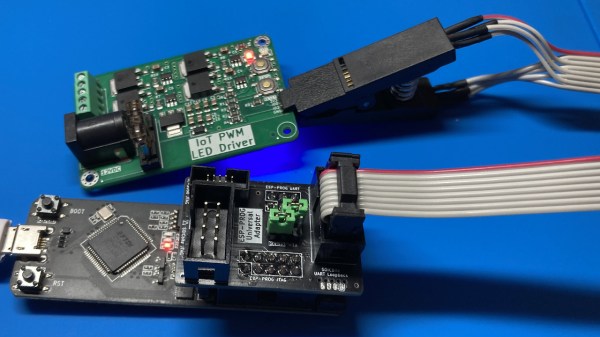
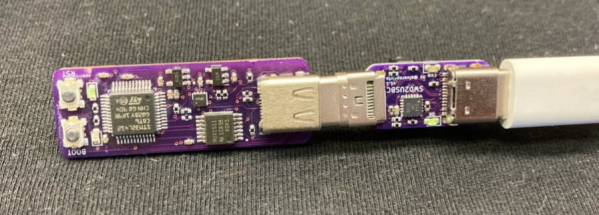
Did you ever struggle with an ESP32 board of yours, wishing you had exposed that UART, or seriously lacking the JTAG port access? If so, you should seriously check out [0xjmux]’s ESP-PROG-Adapter project, because [0xjmux] has put a lot of love and care into making your ESP32 hardware interfacing a breeze. This project shows you how to add JTAG and UART headers with extra low board footprint impact, gives you a KiCad library to do so super quickly, and shares a simple and helpful adapter PCB you can directly use with the exceptionally cheap Espressif’s ESP-Prog dongle you should have bought months ago.
The hardware is perfect for ZIF no-soldering interfacing – first of all, both UART and JTAG can be connected through a SOICBite connection, a solderless connector idea that lets you use SPI flashing clips on specially designed pads at the edge of your board. For the fancy toolkit hackers among us, there’s also a Tag Connect symbol suggested and a connector available, but it carries JTAG that you will already get with the SOICBite, so it’s maybe not worth spending extra money on.
Everything is fully open-source, as one could hope! If you’re doing ESP32 hacking, you simply have to order this board and a SOIC clip to go with it, given just how much trouble [0xjmux]’s board will save you when programming or debugging your ESP32 devices. Now, you don’t strictly need the ESP-Prog dongle – you could remix this into an adapter for the Pi Pico board instead. Oh, and if designing boards with ARM CPUs are your thing, you might benefit from being reminded about the Debug Edge standard!