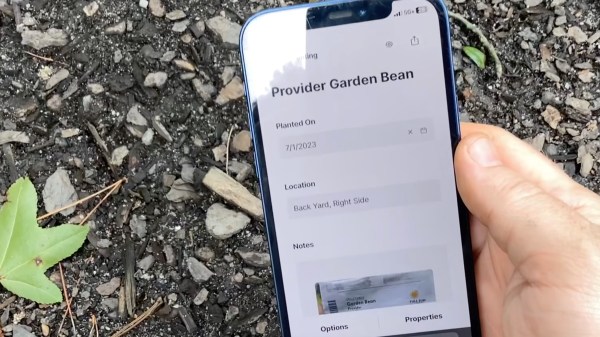
Sometimes we have a new part or piece of tech that we want to use, and it feels like a solution looking for a problem. Upon first encountering NFC Tags, [nalanj] was looking for an application and thought they might make a great update to old-fashioned plant markers in a garden. Those are usually small and, being outside 24/7, the elements tend to wear away at what little information they hold.

[nalanj] used a freeform data structuring service called Cardinal to set up text information fields for each plant and even photos. Once a template has been created, every entry gets a unique URL that’s perfect for writing to an NFC tag. See the blog post on Cardinal’s site for the whole process, the thought behind the physical design of the NFC tag holder, and a great application of a pause in the 3D print to encapsulate the tags.
NFC tags are super hackable, though, so you don’t have to limit yourself to lookups in a plant database. Heck, you could throw away your door keys.