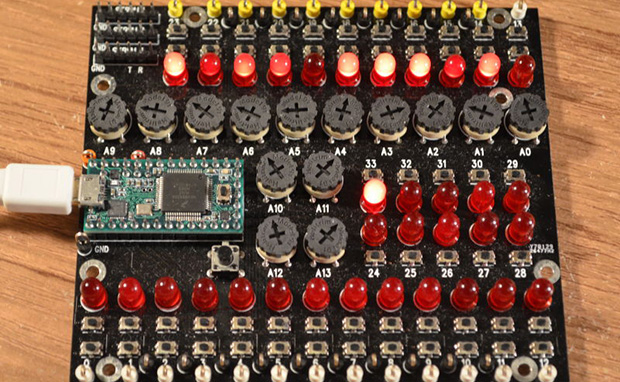
[Paul Stoffregen], creator of the Teensy series of dev boards, previously implemented a six-axis joystick for Teensyduino, the Arduino library for the Teensy. He had originally tried 8 axes, but a few problems cropped up, deadlines approached, and he left it as is. A few recent projects gave him some insight into how to implement a joystick with more than six axes as a USB HID device, so he started looking at how to read an improbable amount of pots and buttons for a USB joystick.
So far, the biggest problem is figuring out what software can actually use an HID joystick with this many controls. The answer to that question is none. The Linux-based jstest-gtk is able to read 6+17 pots, the four hat switches, but only 64 of the 128 buttons. A user on the Teensy forums, [Pointy], has been working on his own joystick test app that works on Linux Windows, but testing the joystick on Windows is an exercise in futility for reasons no one can figure out.
As for why anyone would want a six-axis, 17-slider, 128-button joystick, think about this: with this much control, it would be relatively simple to build the MIDI controller to end all MIDI controllers, or a cockpit simulator for everything from a C172, 737, to a Kerbal interplanetary cruiser. That’s an impressive amount of control, and all from a $20 Teensy dev board.
Further testing of this Teensy joystick is desperately needed, so if you’re able to help out drop a note in the forum thread.