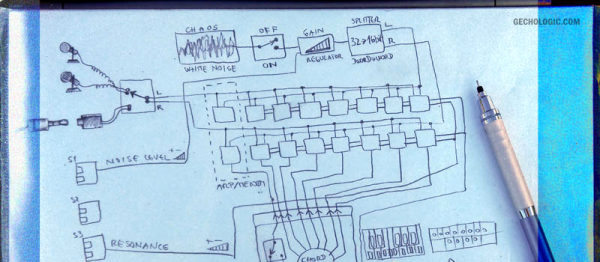
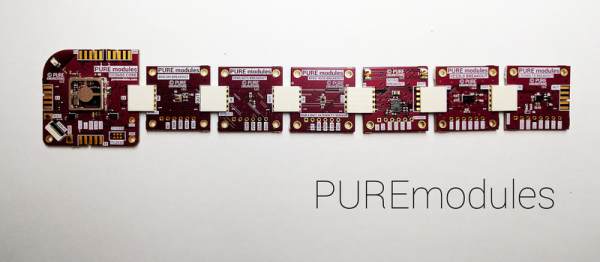
Possibly the greatest hacker show on Earth, the 33rd annual Chaos Communication Congress (33C3) begins Tuesday morning in Hamburg, Germany. And Hackaday will be there! Contributing Editor [Elliot Williams] is taking the night train up and will be trying to take it all in for you. The schedule looks tremendous.
If you can’t make it, don’t fret. There will be live streaming, and the talks are usually available in preliminary edit for viewing or download just a few minutes after they finish. It’s even cooler to watch the talks with friends, though. Every hackerspace with a video projector could be playing along, live or after the fact. Pick some cool talks and have a “movie night”.
 If you’re going to be in Hamburg, and you want to show us something cool, tell us that something is NOTAHACK!1!! in person, or even just say “Hi”, we’ll be wandering around from talk to talk and session to session just like you, only with a backpack full of Hackaday stickers.
If you’re going to be in Hamburg, and you want to show us something cool, tell us that something is NOTAHACK!1!! in person, or even just say “Hi”, we’ll be wandering around from talk to talk and session to session just like you, only with a backpack full of Hackaday stickers.
If there’s anything you think we should see, post up in the comments. If there’s enough call for it, we’ll have a Hackaday meetup once we can figure out a good time and location. Bring us a cool hack, and we’ll document it on the spot! Our DECT phone number is 2475.