Aside from apparently having both the ability to reproduce on their own and simultaneously never being around when you need one, USB chargers seem innocuous enough. The specs are simple: convert mains voltage to 5 volts, and don’t kill anyone while doing it. Both specs are typically met by most designs, but judging by [DiodeGoneWild]’s latest USB charger teardown, the latter only just barely, and with a whole lot of luck.
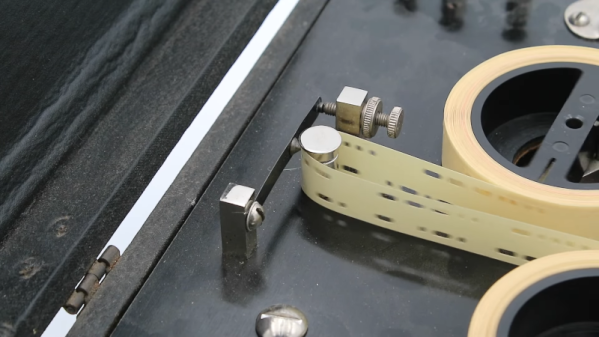
The sad state of plug-in USB power supplies is one of [DiodeGoneWild]’s pet gripes, and deservedly so. Most USB chargers cram a lot of electronics into a mighty small volume, and are built to a price point, meaning that something has to give in the design. In the case of the two units he tears apart in the video below, it’s pretty clear where the compromises are. Neither unit met the specs on the label in terms of current supplied and voltage regulation, even the apparently more capable quick charger, which is the first to go under the knife. The PCB within holds some alarming surprises, like the minimal physical isolation between the mains part of the circuit and the low-voltage section, but the real treat is the Schottky diode that gets up to 170°C under full load. Safety tip: when you smell plastic burning, throw the thing out.
The second charger didn’t fare any better; although it didn’t overheat, that’s mainly because it shut itself off before it could deliver a fraction of its rated 1 amp output. The PCB construction was shoddy in the extreme, with a squiggly trace standing in for a proper fuse and a fraction of a millimeter separation between primary and secondary traces. The flyback transformer was a treat, too; who doesn’t want to rely on a whisper-thin layer of cheap lacquer to keep mains voltage out of your phone?
All in all, these designs are horrible, and we have to thank [DiodeGoneWild] for the nightmares we’ll have whenever we plug into one of these things from now on. On the other hand, this was a great introduction to switch-mode power supply designs, and what not to do with our own builds. Continue reading “Just How Dodgy Are Cheap USB Chargers Anyway?”