Right now, you can get a diode laser engraver on eBay for around $100 USD. That sounds like a deal, but it’ll probably use some arcane proprietary software, won’t be terribly accurate, and the laser itself will almost certainly be fully exposed. Of course there’s no shortage of DIY builds which improve upon this situation greatly, but unfortunately the documentation and instructions to replicate them yourself often leave a lot to be desired.
To get a safe and accurate laser platform into the hands of hackers everywhere, we need more well documented open source designs that are actually built with community in mind. Projects like the Engravinator from [Adam Haile]. This isn’t a one-off design with documentation thrown together after the fact, it’s a fully open hardware engraver with a concise assembly guide that’s built from 3D printed parts and readily available components. You’re free to source and print the parts yourself or, eventually, purchase everything as a kit.

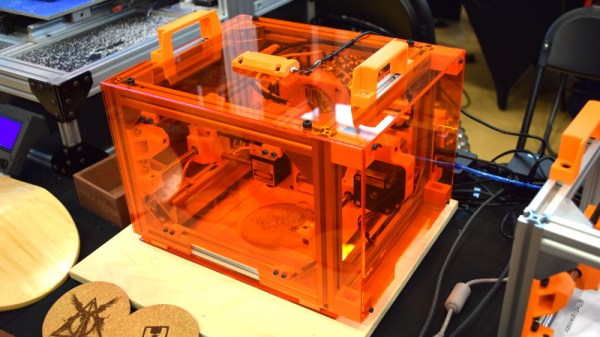
The microwave-sized Engravinator is built from standard 2020 aluminum extrusion, and offers a workable area of 130mm x 130mm. There’s a hatch on the front of the enclosure for objects that are small enough to fit inside the machine, but the open bottom and handles on the top also allow the user to place the Engravinator directly onto the work surface. [Adam] says this feature can be especially useful if you’re looking to burn a design into a tabletop or other large object.
Outside of the aluminum extrusion and miscellaneous hardware that make up the frame, most of the other parts are 3D printed. Released under the CERN Open Hardware License v1.2 and distributed as both STL and STEP files, the printable parts for the Engravinator are ripe for modification should you be so inclined. The same goes for the DXF files for the enclosure panels, which will need to be cut out of orange acrylic with a CNC or (ironically) a laser.
Continue reading “An Open Hardware Laser Engraver For Everyone”











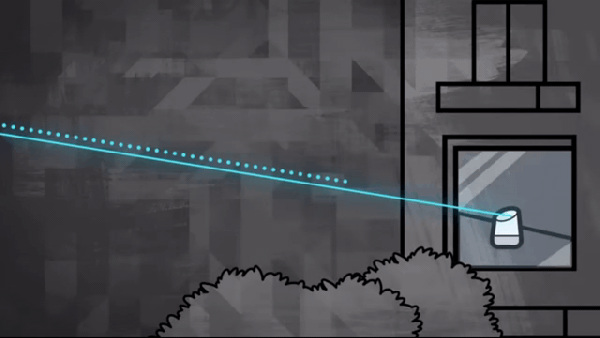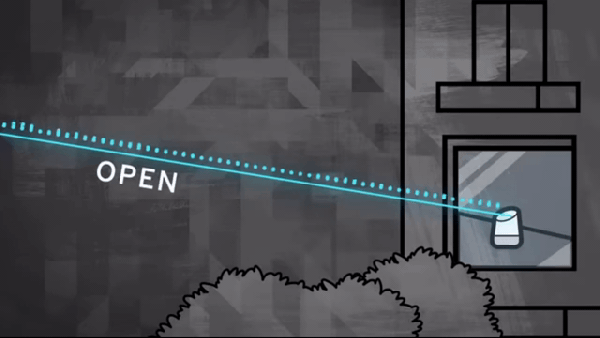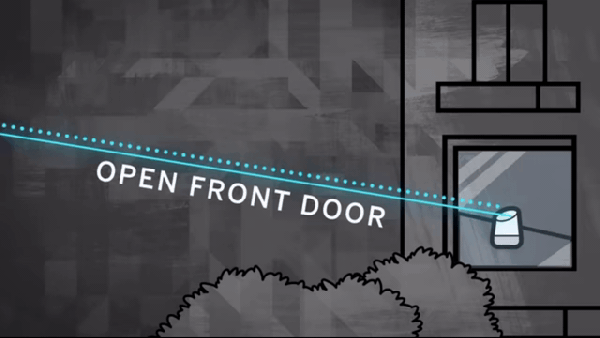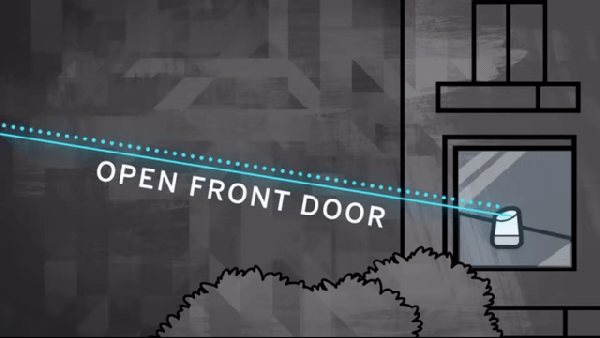
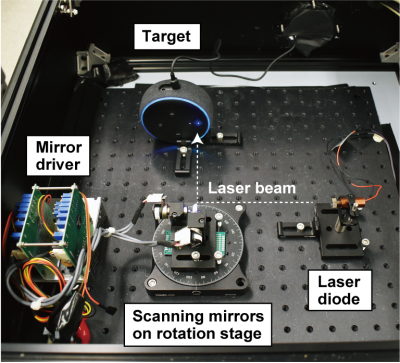 In one of the cooler hacks we’ve seen recently, a bunch of hacking academics at the University of Michigan researched the ability to flicker a laser at audible sound frequencies to see if they could remotely operate microphones simply by shining a light on them.
In one of the cooler hacks we’ve seen recently, a bunch of hacking academics at the University of Michigan researched the ability to flicker a laser at audible sound frequencies to see if they could remotely operate microphones simply by shining a light on them. 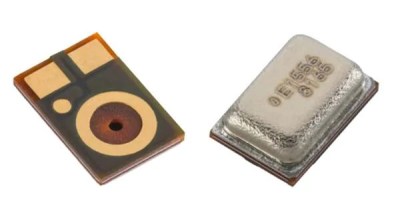 Knowles SPV0842LR5H. This attack is relatively easy to prevent; manufacturers would simply need to install screens to prevent light from hitting the microphones. For devices already installed in our homes, we recommend either putting a cardboard box over them or moving them away from windows where unscrupulous neighbors or KGB agents could gain access. This does make us wonder if MEMS mics are also vulnerable to radio waves.
Knowles SPV0842LR5H. This attack is relatively easy to prevent; manufacturers would simply need to install screens to prevent light from hitting the microphones. For devices already installed in our homes, we recommend either putting a cardboard box over them or moving them away from windows where unscrupulous neighbors or KGB agents could gain access. This does make us wonder if MEMS mics are also vulnerable to radio waves.








