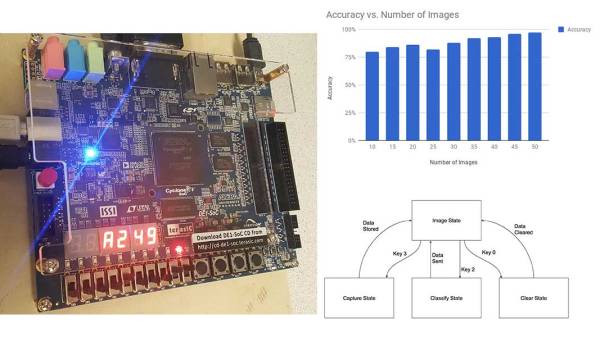
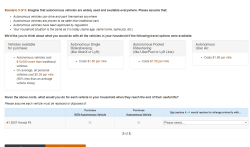
The history of aviation is full of notable X-Planes, a number of which heralded in new generations of flight. The Bell X-1 became the first aircraft to break the speed of sound during level flight in 1947 with the legendary Charles “Chuck” Yeager at the controls. A few years later the X-2 would push man up to Mach 3, refining our understanding of supersonic flight. In the 1960’s, the North American built X-15 would not only take us to the edge of space, but set a world speed record which remains unbroken.
Compared to the heady post-war days when it seemed the sky was quite literally the limit, X-Planes in the modern era have become more utilitarian in nature. They are often proposed but never built, and if they do get built, the trend has been towards unmanned subscale vehicles due to their lower cost and risk. The few full-scale piloted X-Planes of the 21st century have largely been prototypes for new military fighter jets rather than scientific research aircraft.
But thanks to a commitment from NASA, the Lockheed Martin X-59 might finally break that trend and become another historic vehicle worthy of the X-Plane lineage. Construction has already begun on the X-59, and the program has recently passed a rigorous design and timeline overview by NASA officials which confirmed the agency’s intent to financially and logistically support the development of the aircraft through their Low Boom Flight Demonstrator initiative. If successful, the X-59 will not only help refine the technology for the next generation of commercial supersonic aircraft, but potentially help change the laws which have prevented such aircraft from operating over land in the United States since 1973.
Continue reading “Shushing Sonic Booms: NASA’s Supersonic X-Plane To Take Flight In 2021”


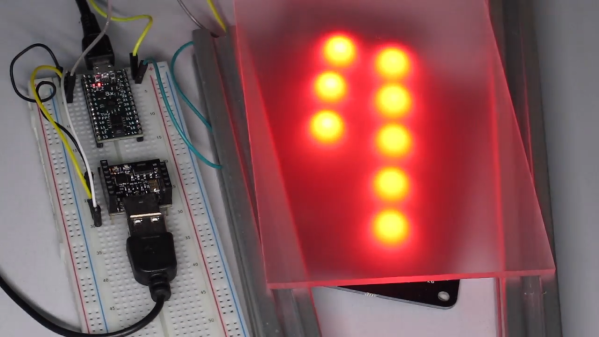

 [William] acknowledges that the build is a bit of a hack job, but the project page does a good job of documenting his build process and covering the kinds of decisions involved in interfacing to a separate piece of hardware. After all, most budding hackers have sooner or later asked themselves “how do I make my gadget press a button on this other thing?” [William] ends up using a small relay to close the connection between the traces for the B button when triggered by a microphone module, but he points out that it should be possible to do a non-destructive version of the mod. Examples exist of
[William] acknowledges that the build is a bit of a hack job, but the project page does a good job of documenting his build process and covering the kinds of decisions involved in interfacing to a separate piece of hardware. After all, most budding hackers have sooner or later asked themselves “how do I make my gadget press a button on this other thing?” [William] ends up using a small relay to close the connection between the traces for the B button when triggered by a microphone module, but he points out that it should be possible to do a non-destructive version of the mod. Examples exist of