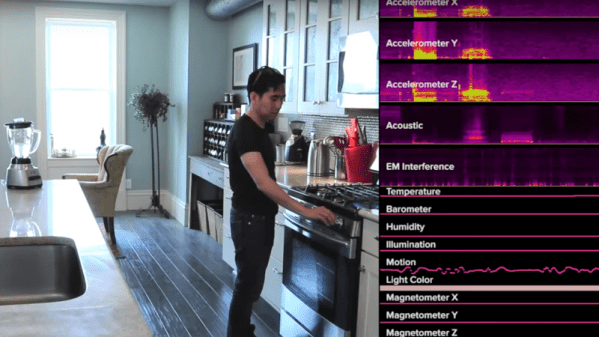
The Arduino has inspired many a creative projects that can be beneficial to humanity. The Arduino Hamster Wheel Pedometer by [John Mueller] on the other hand is a creation that is meant for the cute furry rodent pets. When [John Mueller]’s daughter wanted to keep track of her hamster’s night-time strolls, her maker-dad saw it as an opportunity to get her involved in technology. The project consists of a hamster-wheel with a magnet that triggers a reed switch on completing a revolution. The entire assembly is custom-made and [John Mueller] does an excellent job documenting the build with a lot of clear images.
The wheel is affixed to a shaft with a ball bearing at one end and the entire thing is mounted on the side of the cage so that it can be removed with ease for maintenance. The reed switch is embedded in the wooden mounting block such that the connecting cables pass from inside the assembly. This prevents the hamster from coming in contact with the cabling or damaging it in any way. An LCD and the Arduino Uno are placed outside the cage and are used to display the revolutions of the wheel as well as the equivalent miles travelled.
The code for the Arduino is also supplied for anyone who wants to replicate the project and the video below shows the working of the project. The project could also be extended to count calories burned as well as running speed. This project is a prime example of how technology can be used to assist and is similar to the IoT Hamster Wheels that tweets every movement of the Hamster Life.
Continue reading “Pedometer For Calorie Conscious Hamster Owners”








 Today’s devices utilize two rather rudimentary parts to provide an interaction with users. The first is how the devices pattern match language; it isn’t all that sophisticated. The other is the trivial nature of many of the apps, or — as Alexa calls them — skills. There are some good ones to be sure, but for every one useful application of the technology, there’s a dozen that are just text-to-speech of an RSS feed. Looking through the skills available we were amused at how many different offerings convert resistor color codes back and forth to values.
Today’s devices utilize two rather rudimentary parts to provide an interaction with users. The first is how the devices pattern match language; it isn’t all that sophisticated. The other is the trivial nature of many of the apps, or — as Alexa calls them — skills. There are some good ones to be sure, but for every one useful application of the technology, there’s a dozen that are just text-to-speech of an RSS feed. Looking through the skills available we were amused at how many different offerings convert resistor color codes back and forth to values.








