Sometimes we hack for the thrill of making something new, and sometimes we hack to push back the dark veil of ignorance to shed fresh light on a problem. And sometimes, like when turning a used label printer into a point-of-sale receipt printer, we hack because we’re cheapskates.
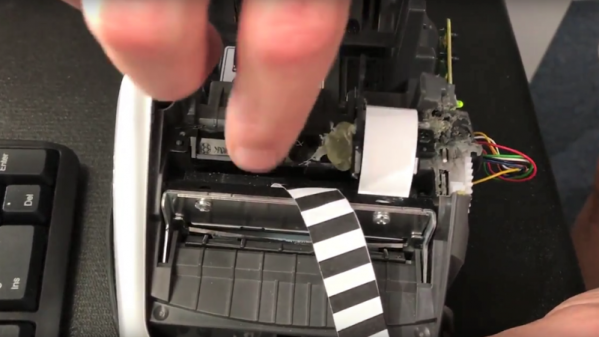
We say that with the utmost respect and affection — there’s nothing to be ashamed of when your motive is strictly pecuniary. In [Dan Herlihy]’s case, hacking a cheap Brother label printer to use thermal paper meant saving $300 on a dedicated receipt printer. But it also meant beating Brother at their “Razor and Blades” business model that keeps you buying their expensive proprietary labels. A pattern of holes in the plastic label roll tells the printer what size labels are loaded, so [Dan] defeated that by breaking off a piece of the plastic and gluing it on the sensor. To convince the printer that plain thermal paper is label stock, he printed up a small strip of paper with the same pattern of black registration stripes that appear on the back of the labels. Pretty clever stuff, and it lets him print high-resolution receipts for his electronics shop on the seriously cheap.
[Dan]’s hack is simple, but may suffer from wear on the paper encoder strip. Perhaps this Brother hack using the gears as encoders will provide some inspiration for long-term fix.
Continue reading “Tightwad Hacks Label Printer, Beats Manufacturer At Own Game”



 The Raspberry Pi uses the camera board plus some forward-pointing laser dots as a rangefinder; as long as at least two laser dots are visible on the subject, the distance between the device and the subject can be calculated. The Pi then uses the knowledge of how near or far the subject is to present a final image whose zoom level has been adjusted to match (and offset) the range of the subject from the camera, in effect canceling out the way an object appears larger or smaller based on distance.
The Raspberry Pi uses the camera board plus some forward-pointing laser dots as a rangefinder; as long as at least two laser dots are visible on the subject, the distance between the device and the subject can be calculated. The Pi then uses the knowledge of how near or far the subject is to present a final image whose zoom level has been adjusted to match (and offset) the range of the subject from the camera, in effect canceling out the way an object appears larger or smaller based on distance.














