When you think about it, for most of human history we’ve been a pretty slow bunch. At any time before about 150 years ago, if you were moving faster than a horse can run, you were probably falling to your death. And so the need to take aerodynamics into consideration is a pretty new thing.
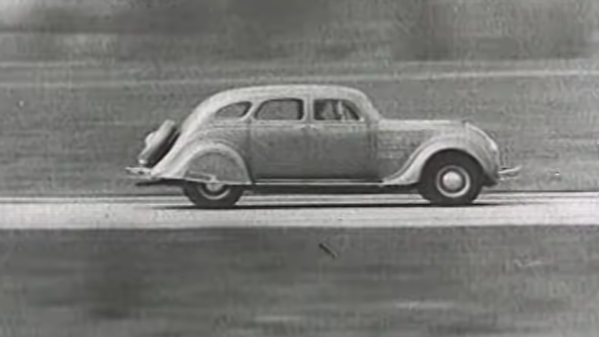
The relative novelty of aerodynamic design struck us pretty hard when we stumbled across this mid-1930s film about getting better performance from cars. It was produced for the Chrysler Sales Corporation and featured the innovative design of the 1934 Chrysler Airflow. The film’s narration makes it clear why the carmaker would go through the trouble of completely rethinking how cars are made; despite doubling average engine horsepower over the preceding decade, cars had added only about 15% to their top speed. And while to our 21st-century eyes, the Chrysler Airflow might look like a bulked-up Volkswagen Beetle, compared to the standard automotive designs of the day, it was a huge aerodynamic leap forward. This makes sense with what else was going on in the technology world at the time — air travel — the innovations of which, such as wind tunnel testing of models, were spilling over into other areas of design. There’s also the influence of [Orville Wright], who was called in to consult on the Airflow design.
While the Airflow wasn’t exactly a huge hit with the motoring public — not that many were built, and very few remain today; [Jay Leno] is one of the few owners, because of course he is — it set standards that would influence automotive designs for the next 80 years. It’s fascinating too that something seemingly as simple as moving the engine forward and streamlining the body a bit took so long to hit upon, and yet yielded so much bang for the buck.
Continue reading “Retrotechtacular: Discovering Aerodynamics With The Chrysler Airflow”