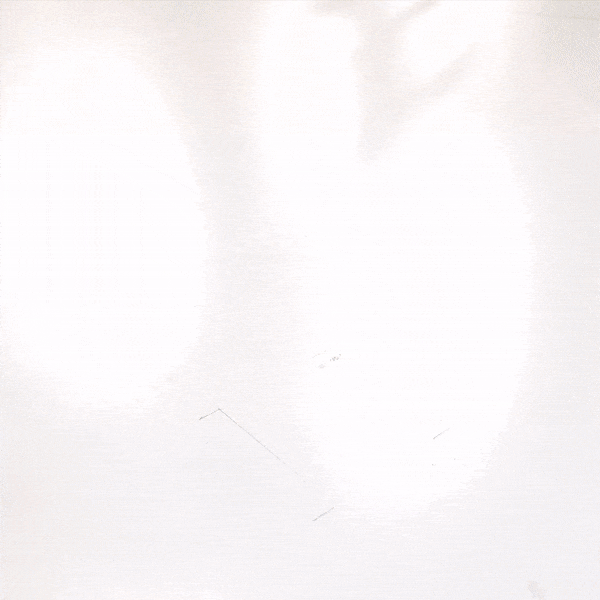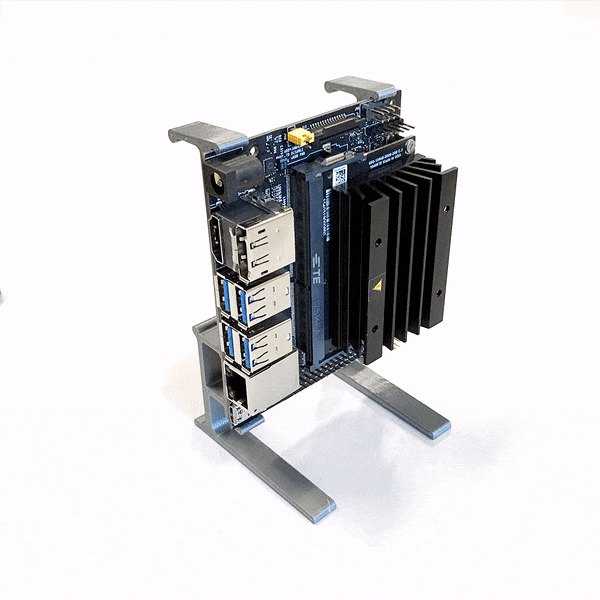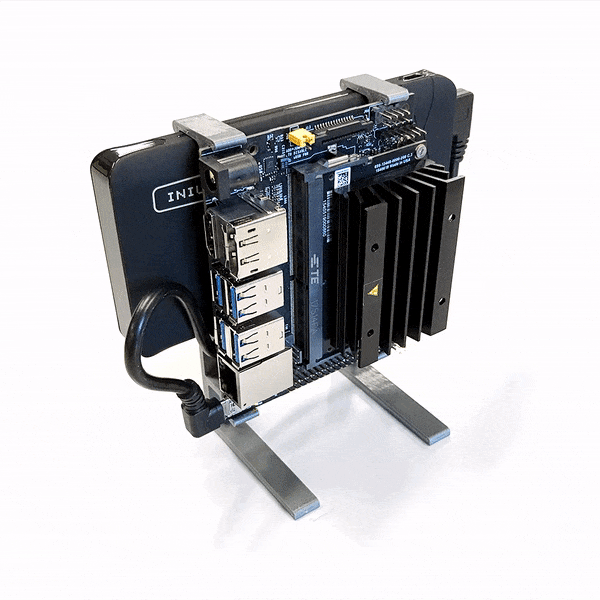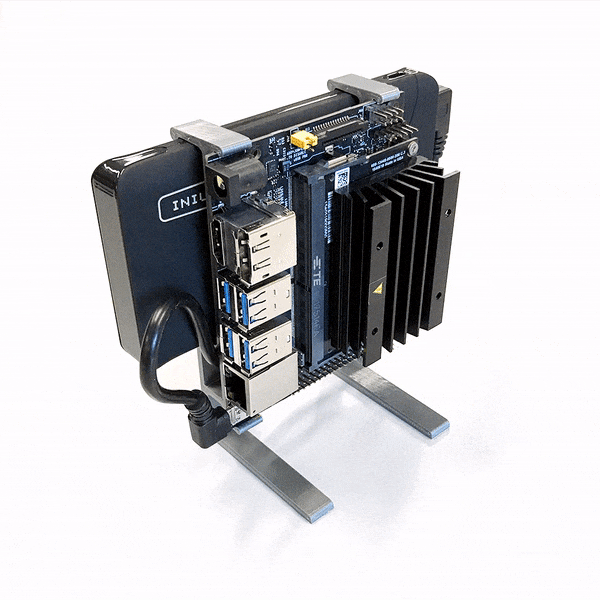Testing is a key part of any product development cycle. Done right, it turns up unknown bugs and problems, and allows for them to be fixed prior to shipment. However, it can be a costly and time-consuming process. The [Bay Libre] team needed to do some work on power management, but the hardware required was just a little on the expensive side. What else does a hacker do, but build their own?
Enter the Thermo-Regulated Power Measurement Platform. It’s a device designed to control the die temperature of a chip during process characterization. This is where a chip, in this case the iMX8MQ, is run at a variety of temperatures, voltages, and frequencies to determine its performance under various conditions. This data guides the parameters used to run the chip in actual use, to best manage its power consumption and thermal performance.
The rig consists of a Peltier element with controller, a heatsink, and a fan. This is lashed up to a series of Python scripts that both control the chip temperature and run through the various testing regimes. Thanks to this automation, what would normally be a day’s work for an engineer can now be completed in just two hours.
Through a few smart component choices, the team accomplished the job at around one-tenth of the cost of commercial grade hardware. Granted, the average hacker probably won’t find themselves doing process characterization for cutting-edge silicon on a regular basis. Still, this project shows the value in building custom hardware to ease the testing process.
Testing is key to success in production. Custom jigs can make for light work when large orders come in, and we’ve run a primer on various testing techniques, too.