While Apple products have their upsides, the major downside with them is their closed environment. Most of the products are difficult to upgrade, to say the least, and this is especially true with the iPhone. While some Android devices still have removable storage and replaceable batteries, this has never been an option for any of Apple’s phones. But that doesn’t mean that upgrading the memory inside the phone is completely impossible.
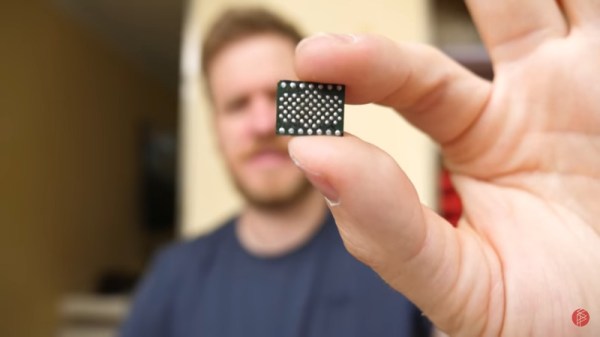
[Scotty] from [Strange Parts] is no stranger to the iPhone, and had heard that there are some shops that can remove the storage chip in the iPhone and replace it with a larger one so he set out on a journey to try this himself. The first step was to program the new chip, since they must have software on them before they’re put in the phone. The chip programmer ironically doesn’t have support for Mac, so [Scotty] had to go to the store to buy a Windows computer first before he could get the chip programmer working right.
After that hurdle, [Scotty] found a bunch of old logic boards from iPhones to perfect his desoldering and resoldering skills. Since this isn’t through-hole technology a lot of practice was needed to desolder the chip from the logic board without damaging any of the other components, then re-ball the solder on the logic board, and then re-soldering the new larger storage chip to the logic board. After some hiccups and a lot of time practicing, [Scotty] finally had an iPhone that he upgraded from 16 GB to 128 GB.
[Scotty] knows his way around the iPhone and has some other videos about other modifications he’s made to his personal phone. His videos are very informative, in-depth, and professionally done so they’re worth a watch even if you don’t plan on trying this upgrade yourself. Not all upgrades to Apple products are difficult and expensive, though. There is one that costs only a dollar.
We sat down with him after his talk at the Hackaday Superconference last November, and we have to say that he made us think more than twice about tackling the tiny computer that lies hidden inside a cell phone. Check out his talk if you haven’t yet.

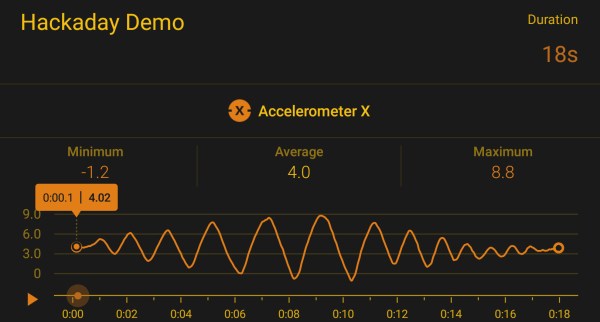


 This comes to our attention because [Pablo] referenced it to modify an
This comes to our attention because [Pablo] referenced it to modify an