Programmers everywhere are familiar with Conway’s Game of Life: whether they’ve written a version themselves or simply seen the mesmerizing action resulting from the cellular automata, it’s a household name in all homes where code is spoken. On Saturday April 11th, 2020 its inventor and namesake, John Horton Conway passed away from COVID-19 at the age of 82.
Born in Liverpool, Conway received his PhD in mathematics in 1964 from Gonville and Caius College, Cambridge. He accepted a position at Sidney Sussex College, Cambridge which he held until joining the faculty of Princeton University in 1987. A brilliant mathematician, he received numerous awards and was well known for his work in combinatorial game theory, group theory, and theoretical physics.
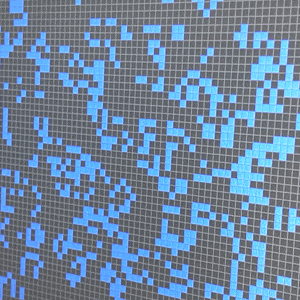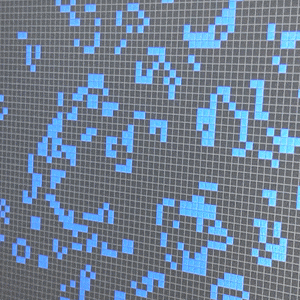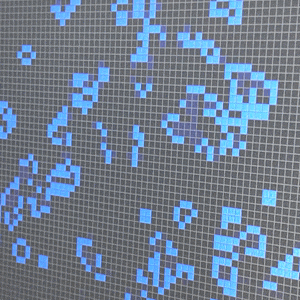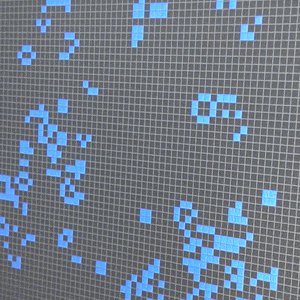 Many readers will be familiar with his Doomsday algorithm which can be used to deduce the day of the week for any given date in your head. But by far the rockstar mathematics moment of developing Conway’s Game of Life in 1970 cements him a perpetual place of legend in computing lore. His original work on the concept used pencil and paper as the computing revolution had yet to make digital resources easily available, even to mathematics researchers like Conway.
Many readers will be familiar with his Doomsday algorithm which can be used to deduce the day of the week for any given date in your head. But by far the rockstar mathematics moment of developing Conway’s Game of Life in 1970 cements him a perpetual place of legend in computing lore. His original work on the concept used pencil and paper as the computing revolution had yet to make digital resources easily available, even to mathematics researchers like Conway.
The game uses an infinite grid of squares where all of the edges of the grid wrap around. Four simple rules (which can be boiled down to three if you’re clever) determine which cells live and which cells die during each frame of the “game”. The only parameters that are needed are the number and position of living cells at the start of the game, and the delay between each game frame. But the effect of this simplicity is not to be understated. The game can be coded by a novice — and it’s become a common challenge in University course work. Small errors, or intentional tweaks, in the implementation have profound effects on behavior of the game. And the effect on the person programming it for the first time can be long lasting. You could call it a mathematics gateway drug, grabbing the curiosity of the unsuspecting mind and pulling it down the rabbit hole of advanced mathematics discovery.
We’d love to celebrate his life by hearing your own stories of programming the Game of Life in the comments below. If you haven’t yet had the pleasure, now’s a great time to take on the challenge.
[Game of Life example shown in this article is John Conway’s Game of Life – 1.0 written in Python by Nick Jarvis and Nick Wayne]