
No, not real birds! [Kyle] works in operations at a web company and needed a way to send alerts to his fellow coworkers, so he modified a flock of Audubon Society plush birds to respond to a Bluetooth beacon.
Using NRF24L01+ Bluetooth Low Energy modules, [Kyle] installed one each in these battery-powered singing birds. The devices are presumably powered off of the battery that comes with the birds, but the use of the BTLE module means the batteries won’t discharge as rapidly.
[Kyle] also built an API that works over HTTP or IRC, which means that the employees in the office can activate everyone else’s birds over a simple and intuitive interface. The birds can be activated one at a time, or all together in “panic” mode as one giant flock (in case of an emergency in the office). They can also be activated one at a time on a specific hour to simulate the Audubon Society’s bird call clock.
He calls the device equail and it’s a very unique notification system with a lot of applications. All of [Kyle]’s code and documentation of his project are available on his github site. He also used this primer on BTLE to get started, and this guide on sending data over BTLE to help get the project in the air.

 With a simple $35 dongle that plugs right into your TV, it’s possible to enjoy your favorite TV shows, YouTube channels, and everything else Chromecast has to offer. Being a WiFi enabled device, it’s also possible to hijack a Chromecast, forcing your neighbors to watch
With a simple $35 dongle that plugs right into your TV, it’s possible to enjoy your favorite TV shows, YouTube channels, and everything else Chromecast has to offer. Being a WiFi enabled device, it’s also possible to hijack a Chromecast, forcing your neighbors to watch 

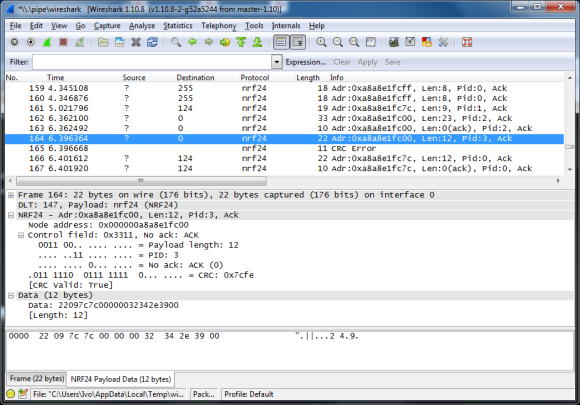
 [Texane] had been thinking about how to monitor the state of his garage door from a remote place. The door itself isn’t around any power outlets, and is a few floors away from where his server would be located in his apartment. This presented a few design challenges – namely, the sensor itself should have a wireless connection to the server, and being low power would be a great idea. This led to the development of a
[Texane] had been thinking about how to monitor the state of his garage door from a remote place. The door itself isn’t around any power outlets, and is a few floors away from where his server would be located in his apartment. This presented a few design challenges – namely, the sensor itself should have a wireless connection to the server, and being low power would be a great idea. This led to the development of a 








