Many of will have marveled at the feats of reverse engineering achieved by decapping integrated circuits and decoding their secrets by examining the raw silicon die. Few of us will have a go for ourselves, but that doesn’t stop the process being a fascinating one. Fortunately [Ryan Cornateanu] is on hand with a step-by-step description of his journey into the art of decapping, as he takes on what might seem an unlikely subject in the form of the CH340 USB to serial chip you’ll find on an Arduino Nano board.
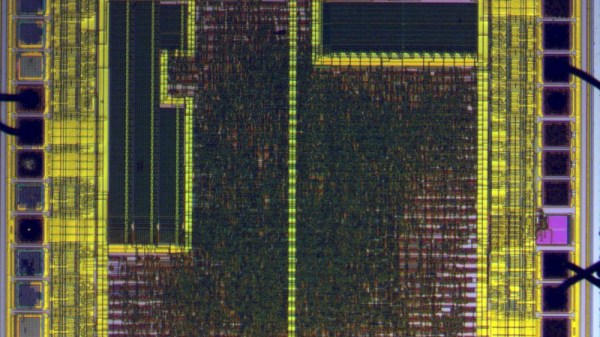
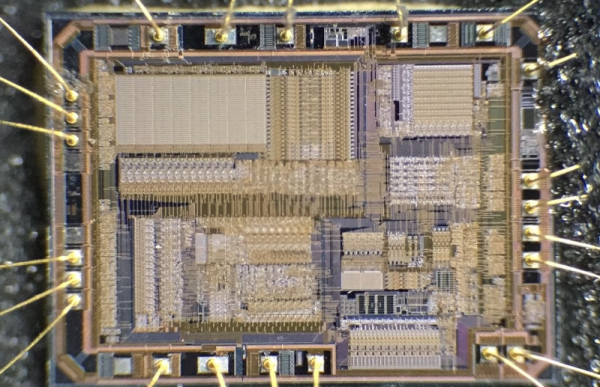
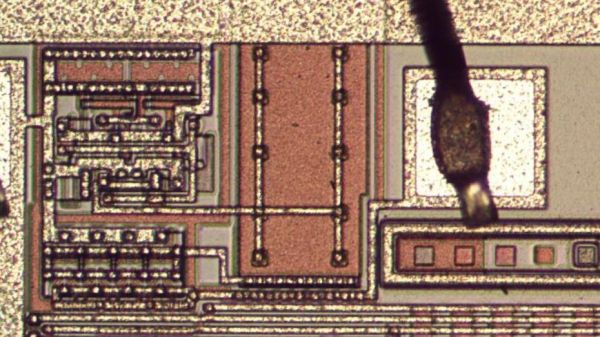
Starting with hot sulphuric acid is probably not everyone’s idea of a day at the bench, but having used it to strip the epoxy from the CH340, he’s able to take a look under the microscope. This is no ordinary microscope but a metallurgists instrument designed to light the top of the sample from one side with polarised light. This allows him to identify an area of mask ROM and zoom in on the transistors that make each individual bit.
At this point the chemistry moves into the downright scary as he reaches for the hydrofluoric acid and has to use a PTFE container because HF is notorious for its voracious reactivity. This allows him to take away the interconnects and look at the transistor layer. He can then with a bit of computer vision processing help extract a bit layer map, which with some experimentation and guesswork can be manipulated into a firmware dump. Even then it’s not done, because he takes us into the world of disassembly of what is an unknown architecture. Definitely worth a read for the armchair chip enthusiast.
If you’re thirsty for more, of course we have to direct you towards the work of [Ken Shirriff].