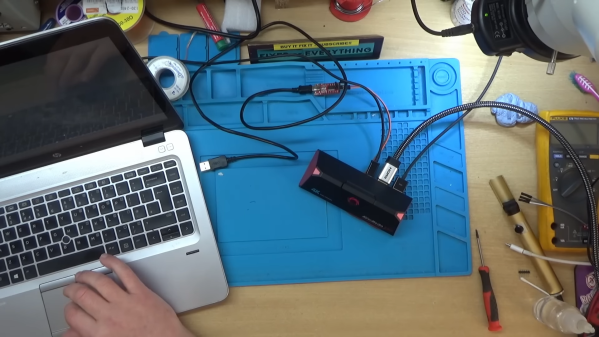
Sometimes, you have a piece of hardware that just up and stops working on you. In today’s fast-paced world, it’s easy to toss something broken and move on. [BuyItFixIt], as you imagine, makes it their purpose to, well, fix things instead. Their latest efforts involved resurrecting a dead AVerMedia Live Gamer 2 Plus capture device sourced off eBay.
The device was advertised as being dead, with no power. Probing around the board when powered up showed that there was some basic activity going on with one of the flash chips, but the device simply wouldn’t spring to life. This suggested that perhaps the flash had become corrupted, which was confirmed when reading the chip mostly returned 0xFF. Sadly, the device was so badly bricked that the usual update methods via SD card simply wouldn’t work.
Eventually, hunting down a debug header provided a way in. [BuyItFixIt] was able to find a way to flash firmware over this connection instead, but there was a problem. The firmware they had was formatted for loading via SD card, and wouldn’t work for the debug mode entry route. Instead, getting the device going would require recovering firmware from a similar working device, and then using that as a guide to assemble a proper workable firmware update to get the device back to an operational state.
It’s a great tale of perseverance and triumph, particularly given many would give up after the first update attempt failed. We’ve seen [BuyItFixIt] pull off some heroic repairs before, too. Video after the break.
Continue reading “Recovering A Busted Video Capture Device With Firmware Flashing Tricks”