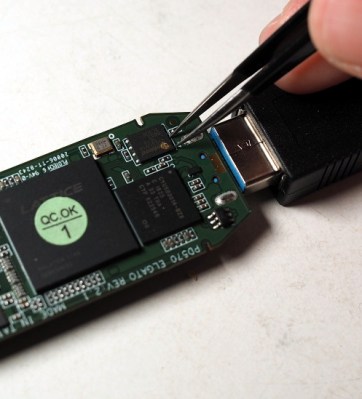
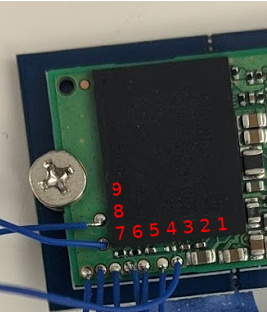
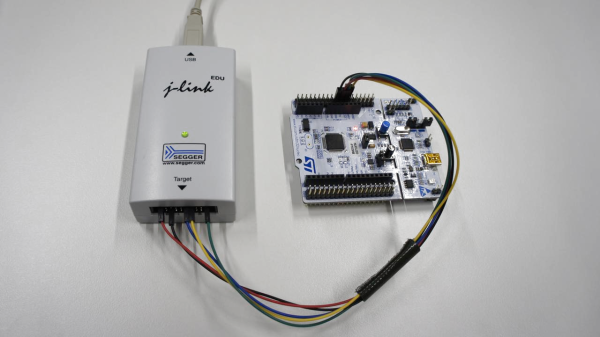
Assistive devices for people with disabilities can make an inestimable difference to their lives, but with a combination of technology, complexity, and often one-off builds for individual needs, they can be eye-wateringly expensive. When the recipient is a young person who may grow out of more than one device as they mature, this cost can be prohibitive. Some way to cut down on the expense is called for, and [Phil Malone] has identified the readily available hoverboard as a possible source of motive power for devices that need it.
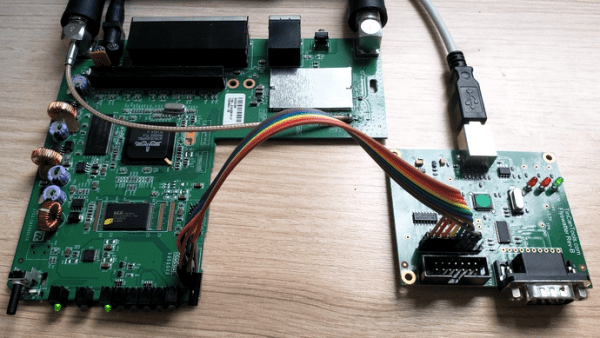
Aside from being a children’s toy, hoverboards have been well and truly hacked; we’ve featured them in Hacky Racers, and as hacker camp transport. But this is an application which demands controllability and finesse not needed when careering round a dusty field. He’s taken that work and built upon it to produce a firmware that he calls HUGS, designed to make the hoverboard motors precisely controllable. It’s a departure from the norm in hoverboard hacking, but perhaps it can open up new vistas in the use of these versatile components.
There is much our community can do when it comes to improving access to assistive technologies, and we hope that this project can be one of the success stories. We would however caution every reader to avoid falling into the engineer savior trap.