If you work at all with British software or hardware engineers, you’ll find that there’s an entire generation perhaps now somewhere between their mid-40s and mid-50s, who stand slightly apart from their peers in their background and experience. These were the lucky teenagers who benefited from the British government’s 1980s push to educate youngsters in computing, and who unlike those before or who followed, arrived at university engineering courses fresh from school fully conversant with every facet of a computer from the hardware upwards.
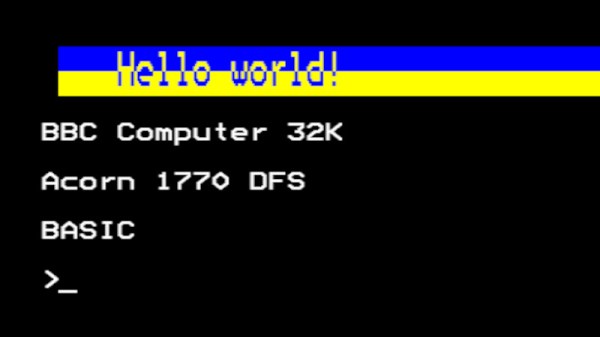
[Alan Pope] is from that generation, and he relates a tale from his youth that wasn’t so out of place back in those days, of how he wrote what we’d now call a simple virus for the BBC Micro. Better still, he’s re-created it.
The post is as much a delightful trip back through that era of microcomputing, including an entertaining aside as he shared an airline journey with BBC Micro designer Chris Turner, and it serves as a reminder of how the BBC Micro’s disk operating system worked. There was a !boot file, which was what would be run from the disk at startup, and his bit of code would subvert that and hide itself in the machine’s so-called sideways RAM. The payload was pretty simple, every 32 soft reboots it would print a “Hello world” message, but it seems that was enough back in 1989 to get him into trouble. The 2023 equivalent works, but we’re guessing no teacher will come for him this time.
If you can’t find a real BBC Micro but still want one on hardware, we’ve brought you an FPGA version in the past.