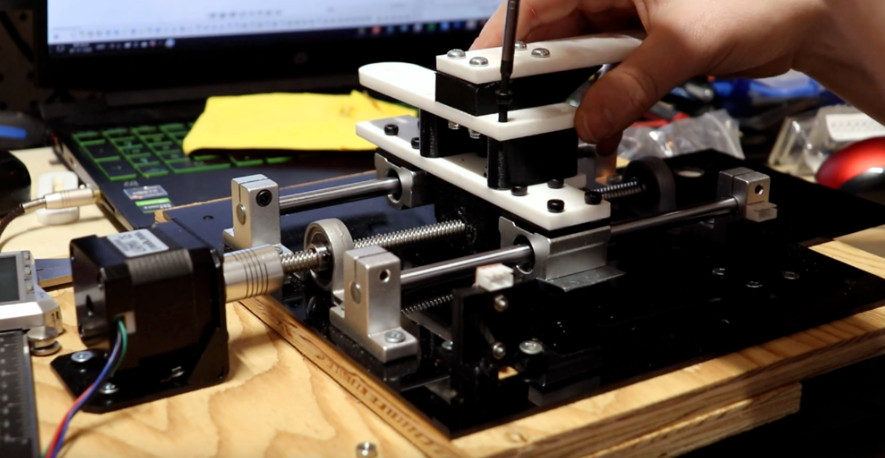
[Lucas VRTech] has made some significant progress with building force-feedback type haptic gloves for use with Steam VR games. The idea is pretty straightforward: the end of the finger is attached to a cable, which is pulled from inside a sprung-loaded spool; the kind used for hanging ID cards on.
The spool body can rotate, but a peg protruding from it engages with the arm of a co-located servo motor. This produces a programmable stop position. But it is a hard stop, and it is not possible with the current hardware to detect precisely when the stop is reached, nor is it possible to control the force it is pushing with. Such features are not difficult to achieve, its just a matter of a little more development with some custom mechatronics.
The current prototype has a focus on cost, which is great as an early development platform. By leveraging 3D printing and off-the-shelf parts that are easy to source; just a handful (chuckle!) of potentiometers, some servo motors and one from any number of ESP32 dev boards and you’re done. The real work is on the software side of things, as the games themselves need to be modified to play ball with the VR glove hardware. This has been achieved with a combination of a custom steam driver they call OpenGloves, and community developed per-game mods. A few titles are available to test right now, so this is definitely something some of us could build in a weekend and get involved with.
The hardware source for the glove mount and per-finger units can be found on the project GitHub, together with the ESP32 source for Arduino.
For some other haptic-related inspiration, here’s a force-feedback mouse, and for a more hand-off feedback, we have a wind-blaster project.
Continue reading “Low Cost Haptic VR Gloves Work With Hacked Steam Games”

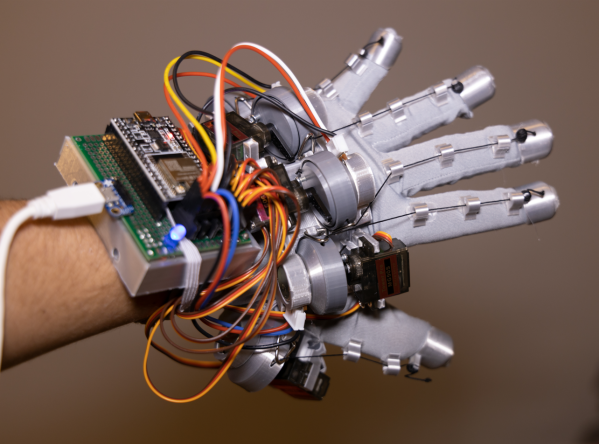
 [Harry Gill] has you covered with
[Harry Gill] has you covered with