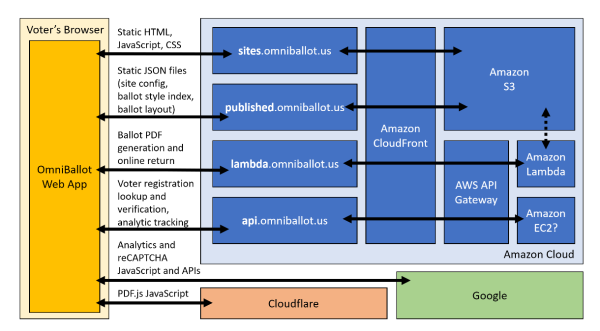
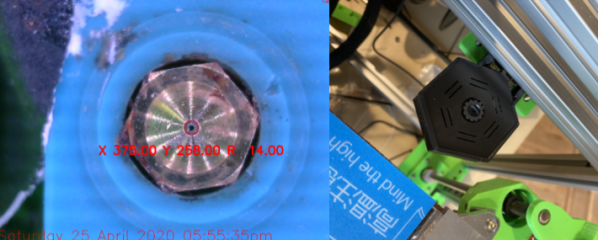
Most folks that have been poking around at multi-tool 3D printing know that lining up nozzles can be a gnarly, but necessary pain point. Existing methods either have us measure offsets with a vernier scale or with a series of pictures taken with an upwards-facing camera. And this step is not to be ignored! Any mismatch between nozzles, and your multicolor prints end up looking like Scotty really screwed up those sliders on that transporter beam console. Fear not, however! [Danal] took this problem as an opportunity to write something that’s completely automated and brought to you by some machine vision.
Dubbed TAMV, for Tool Align Machine Vision, [Danal] added a Raspberry Pi alongside his existing 3D printing motion controller in addition to an upwards facing camera. A few lines of code (and a few hours of compiling OpenCV) later, and he had himself a circle-detecting script that automatically cycles through each tool, detects the nozzle center, and calculates an offset for each tool that’s stored into the machine’s configuration file. If that’s not nifty enough, he’s made the entire setup open-source, and he included both an installation script for compiling OpenCV and a well-written set of step-by-step instructions.
In a world where most hobbyists approaches still solve this problem manually, this is leaps and bounds ahead of what we know, and it’s a great application of machine vision built on top of a stack of recognizable hardware and software. While this project was outfitted for a Jubilee running a Duet3 controller with a Raspberry Pi connected in “single-board computer” mode, the core features are readily adaptable to any other multi-tool machine with a similar control board stack. And for folks willing to poke under the hood, the project could even be extended to a standalone script that you can run on your PC locally to simply print the tool offsets separately.
Alongside TAMV, it’s refreshing that even a decade after 3D printers have been with us, we’re still finding ways to make these machines more capable. For more fresh hacks in this category, check out a new spin on using sharpie ink as a support material release agent.
Sadly, [Danal] has recently passed away in the last week, but we are grateful to capture a snapshot in the history of this person’s life.
Continue reading “Dial In Your Multi-Headed 3D Printer With 2020 Machine Vision” →