Do humanoid robots dream of electric retirement? Who knows, but maybe we can ask Boston Dynamics’ Atlas HD, which was officially retired this week. The humanoid robot, notable for its warehouse Parkour and sweet dance moves, never went into production, at least not as far as we know. Atlas always seemed like it was intended to be an R&D platform, to see what was possible for a humanoid robot, and in that way it had a heck of a career. But it’s probably a good thing that fleets of Atlas robots aren’t wandering around shop floors or serving drinks, especially given the number of hydraulic blowouts the robot suffered. That also seems to be one of the lessons Boston Dynamics learned, since Atlas’ younger, nimbler replacement is said to be all-electric. From the thumbnail, the new kid already seems pretty scarred and battered, so here’s hoping we get to see some all-electric robot fails soon.
MXM: Powerful, Misused, Hackable
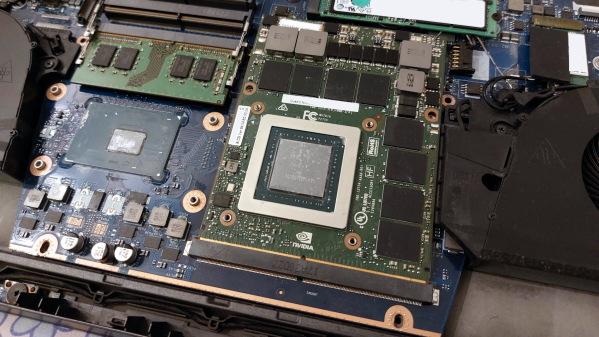
Today, we’ll look into yet another standard in the embedded space: MXM. It stands for “Mobile PCI Express Module”, and is basically intended as a GPU interface for laptops with PCIe, but there’s way more to it – it can work for any high-power high-throughput PCIe device, with a fair few DisplayPort links if you need them!
You will see MXM sockets in older generations of laptops, barebones desktop PCs, servers, and even automotive computers – certain generations of Tesla cars used to ship with MXM-socketed Nvidia GPUs! Given that GPUs are in vogue today, it pays to know how you can get one in low-profile form-factor and avoid putting a giant desktop GPU inside your device.
I only had a passing knowledge of the MXM standard until a bit ago, but my friend, [WifiCable], has been playing with it for a fair bit now. On a long Discord call, she guided me through all the cool things we should know about the MXM standard, its history, compatibility woes, and hackability potential. I’ve summed all of it up into this article – let’s take a look!
This article has been written based on info that [WifiCable] has given me, and, it’s also certainly not the last one where I interview a hacker and condense their knowledge into a writeup. If you are interested, let’s chat!
VCF East 2024 Was Bigger And Better Than Ever
I knew something had changed before I even paid for my ticket to this year’s Vintage Computer Festival East at the InfoAge Science and History Museum in Wall, New Jersey.
Over the last couple of years, attendance has been growing to the point that parking in the lot directly next to the main entrance has been reserved for only the earliest of risers. That hasn’t described yours truly since the days when I still had what my wife refers to as a “real job”, so that’s meant parking in the overflow lot down the road and walking the half a mile or so back to the main gate. Penance for working on the Internet, let’s call it.
 But this time, while walking along the fence that surrounds the sprawling InfoAge campus, I came across an open gate and a volunteer selling tickets. When commenting to her that this was a pleasant surprise compared to the march I’d anticipated, she responded that there had been so many people trying to get into the main entrance that morning that they decided to station her out here to handle the overflow.
But this time, while walking along the fence that surrounds the sprawling InfoAge campus, I came across an open gate and a volunteer selling tickets. When commenting to her that this was a pleasant surprise compared to the march I’d anticipated, she responded that there had been so many people trying to get into the main entrance that morning that they decided to station her out here to handle the overflow.
I was a few steps past her table and into InfoAge before the implications of this interaction really hit me. Two entrances. How many attendees does there need to be before you setup a secondary ticket booth out by the reserve parking lot just to keep things moving smoothly? Well, I can’t tell you what the exact number is. But after spending the rest of the day walking between all the buildings it took to contain all of the exhibits, talks, and activities this year, I can tell you it’s however many people came to VCF East 2024.
Compared to its relatively humble beginnings, it’s incredible to see what this event has grown into. InfoAge was packed to the rafters, and despite what you might think about a festival celebrating decades old computing hardware, there were plenty of young faces in the crowd. I’m not sure exactly what’s changed, but the whole place was positively jumping. Perhaps it’s partially the generational nostalgia that’s kept Netflix cranking out new seasons of the 1980’s set Stranger Things. I’m sure attention (and attendance) from several well known YouTube personalities have played a big part as well.
Whatever the magic formula that’s turned what was once a somewhat somber retrospective on early desktop computers into a major destination for tech lovers, I’m all for it. Love Live the Vintage Computer Festival!
Continue reading “VCF East 2024 Was Bigger And Better Than Ever”
Human-Interfacing Devices: HID Over I2C
In the previous two HID articles, we talked about stealing HID descriptors, learned about a number of cool tools you can use for HID hacking on Linux, and created a touchscreen device. This time, let’s talk about an underappreciated HID standard, but one that you might be using right now as you’re reading this article – I2C-HID, or HID over I2C.
HID as a protocol can be tunneled over many different channels. If you’ve used a Bluetooth keyboard, for instance, you’ve used tunneled HID. For about ten years now, I2C-HID has been heavily present in laptop space, it was initially used in touchpads, later in touchscreens, and now also in sensor hubs. Yes, you can expose sensor data over HID, and if you have a clamshell (foldable) laptop, that’s how the rotation-determining accelerometer exposes its data to your OS.

In modern world of input devices, I2C-HID is spreading, and the coolest thing is that it’s standardized. The standardization means a lot of great things for us hackers. For one, unlike all of those I2C touchscreen controllers, HID-I2C devices are easier to reuse; as much as information on them might be lacking at the moment, that’s what we’re combating right now as we speak! If you are using a recent laptop, the touchpad is most likely I2C-HID. Today, let’s take a look at converting one of those touchpads to USB HID.
A Hackable Platform
Cyberpunk Guitar Strap Lights Up With Repurposed PCBs
Sometimes, whether we like it or not, ordering PCBs results in extra PCBs lying around, either because of board house minimums, mistakes on either end, or both. What’s to be done with these boards? If you’re Hackaday alum [Jeremy Cook], you make a sound-reactive, light-up guitar strap and rock out in cyberpunk style.
The PCBs in question were left over from [Jeremy]’s JC Pro Macro project, and each have four addressable RGB LEDs on board. These were easy enough to chain together with jumper wires, solder, and a decent amount of hot glue. Here’s a hot tip: you can use compressed air to rapidly cool hot glue if you turn the can upside down. Just don’t spray it on your fingers.
The brains of this operation is Adafruit Circuit Playground Express, which runs off of a lipstick battery and conveniently brings a microphone to the table. These two are united by a 3D print, which is hot-glued to the guitar strap along with all the boards. In the second video after the break, there’s a bonus easy-to-make version that uses an RGB LED strip in place of the repurposed PCBs. There’s no solder or even hot glue involved.
Want to really light up the night? Print yourself a sound-reactive LED guitar.
Continue reading “Cyberpunk Guitar Strap Lights Up With Repurposed PCBs”
Linux Fu: Stupid Systemd Tricks
Last time, I gave a whirlwind introduction to a very small slice of systemd. If you aren’t comfortable with systemd services, timers, and mounts, you might want to read that now. Otherwise, press on to see a few interesting uses for custom systemd units, including running a few things on a schedule and automatically mounting a Raspberry Pi Zero.
Can you do every one of these things in a different way? Of course you can. I’m not debating the relative merits of using or not using systemd. However, unless you totally control your own environment, good chance you are going to have to interact with systemd at some point.
Stupid Trick #1: Update Your IP Address
A few years ago, I talked about updating your remote DNS server with your public IP address. This lets you refer to a hostname like snoopy.hackaday.com and get back to your computer that often changes IP addresses. Sure, you can get services to do that for you, but you must either pay or agree to read ads on their site to keep your hostname going. This is all under your control. In the original post, I suggested using cron or NetworkManager to run the update script. I also hinted you could do it with systemd, but I didn’t tell you how. Let’s fix that.
Logic Analyzers: Decoding And Monitoring
Last time, we looked into using a logic analyzer to decode SPI signals of LCD displays, which can help us reuse LCD screens from proprietary systems, or port LCD driver code from one platform to another! If you are to do that, however, you might find a bottleneck – typically, you need to capture a whole bunch of data and then go through it, comparing bytes one by one, which is quite slow. If you have tinkered with Pulseview, you probably have already found an option to export decoded data – all you need to do is right-click on the decoder output and you’ll be presented with a bunch of options to export it. Here’s what you will find:
2521888-2521888 I²C: Address/data: Start
2521896-2521947 I²C: Address/data: Address write: 22
2521947-2521954 I²C: Address/data: Write
2521955-2521962 I²C: Address/data: ACK
2521962-2522020 I²C: Address/data: Data write: 01
2522021-2522028 I²C: Address/data: ACK
2522030-2522030 I²C: Address/data: Start repeat
2522038-2522089 I²C: Address/data: Address read: 22
2522089-2522096 I²C: Address/data: Read
2522096-2522103 I²C: Address/data: ACK
2522104-2522162 I²C: Address/data: Data read: 91
2522162-2522169 I²C: Address/data: NACK
2522172-2522172 I²C: Address/data: Stop
Whether on the screen or in an exported file, the decoder output is not terribly readable – depending on the kind of interface you’re sniffing, be it I2C, UART or SPI, you will get five to ten lines of decoder output for every byte transferred. If you’re getting large amounts of data from your logic analyzer and you want to actually understand what’s happening, this quickly will become a problem – not to mention that scrolling through the Pulseview window is not a comfortable experience.
The above output could look like this: 0x22: read 0x01 ( DEV_ID) = 0x91 (0b10010001). Yet, it doesn’t, and I want to show you how to correct this injustice. Today, we supercharge Pulseview with a few external scripts, and I’ll show you how to transfer large amounts of Sigrok decoder output data into beautiful human-readable transaction printouts. While we’re at it, let’s also check out commandline sigrok, avoiding the Pulseview UI altogether – with sigrok-cli, you can easily create a lightweight program that runs in the background and saves all captured data into a text file, or shows it on a screen in realtime! Continue reading “Logic Analyzers: Decoding And Monitoring”