It never seems to fail: at the very moment that human society seems to reach a new pinnacle of pettiness, selfishness, violence, and self-absorption, Mother Nature comes along and reminds us all who’s really in charge. The obvious case in point here is the massive earthquakes near the border of Turkey and Syria, the appalling loss of life from which is only now becoming evident, and will certainly climb as survivors trapped since the Monday quakes start to succumb to cold and starvation.
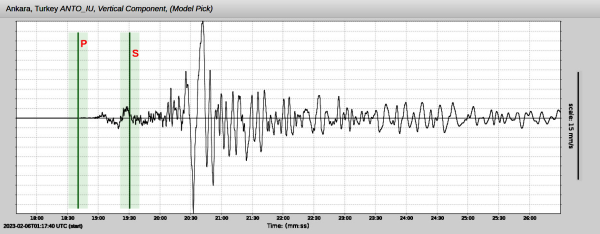
Whatever power over nature we think we can wield pales by comparison with the energy released in this quake alone, which was something like 32 petajoules. How much destruction such a release causes depends on many factors, including the type of quake and its depth, plus the soil conditions at the epicenter. But whatever the local effects on the surface, quakes like these have a tendency to set the entire planet ringing like a bell, with seismic waves transmitted across the world that set the needles of professionally maintained seismometers wiggling.
For as valuable as these seismic networks are, though, there’s a looser, ad hoc network of detection instruments that are capable of picking up quakes as large as these from half a planet away. Some are specifically built to detect Earth changes, while some are instruments that only incidentally respond to the shockwaves traveling through the planet. And we want to know if this quake showed up in the data from anyone’s instruments.
Continue reading “Ask Hackaday: Incidental Earthquake Detection”