Looking to capitalize on his familiarity with the Raspberry Pi, [Sebastian Zen Tatum] decided to put the diminutive Pi Zero at the heart of his “antweight” fighting robot, $hmoney. While it sounds like there were a few bumps in the road early on, the tuxedoed bot took home awards from the recent Houston Mayhem 2021 competition, proving the year of Linux on the battle bot is truly upon us.
Compared to using traditional hobby-grade RC hardware, [Sebastian] says using the Pi represented a considerable cost savings. With Python and evdev, he was able to take input from a commercial Bluetooth game controller and translate it into commands for the GPIO-connected motor controllers. For younger competitors especially, this more familiar interface can be seen as an advantage over the classic RC transmitter.
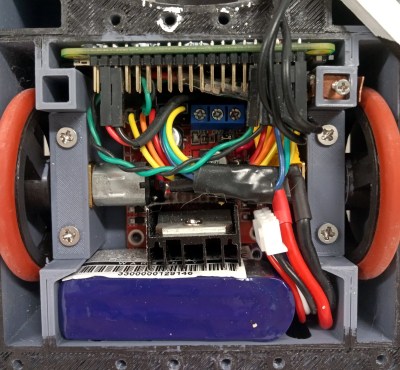 A L298N board handles the two N20 gear motors that provide locomotion, while a Tarot TL300G ESC is responsible for spinning up the brushless motor attached to the “bow tie” spinner in the front. Add in a Turnigy 500mAh 3S battery pack, and you’ve got a compact and straightforward electronics package to nestle into the robot’s 3D printed chassis.
A L298N board handles the two N20 gear motors that provide locomotion, while a Tarot TL300G ESC is responsible for spinning up the brushless motor attached to the “bow tie” spinner in the front. Add in a Turnigy 500mAh 3S battery pack, and you’ve got a compact and straightforward electronics package to nestle into the robot’s 3D printed chassis.
In a Reddit thread about $hmoney, [Sebastian] goes over some of the lessons his team has learned from competing with their one pound Linux bot. An overly ambitious armor design cost them big at an event in Oklahoma, but a tweaked chassis ended up making them much more competitive.
There was also a disappointing loss that the team believes was due to somebody in the audience attempting to pair their phone with the bot’s Pi Zero during the heat of battle, knocking out controls and leaving them dead in the water. Hopefully some improved software can patch that vulnerability before their next bout, especially since everyone that reads Hackaday now knows about it…
While battles between these small-scale bots might not have the same fire and fury of the televised matches, they’re an excellent way to get the next generation of hackers and engineers excited about building their own hardware. We wish [Sebastian] and $hmoney the best of luck, and look forward to hearing more of their war stories in the future.