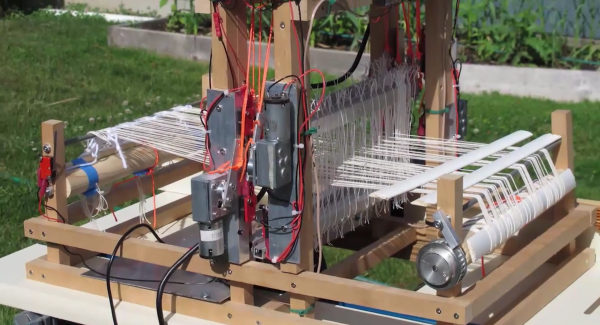
We all maintain this balancing act between the cool things we want, the money we can spend, and our free time. When the pièce de résistance is a couple of orders of magnitude out of our budget, the only question is, “Do I want to spend the time to build my own?” [Nick Charlton] clearly answered “Yes,” and documented the process for his Nautilus speakers. The speaker design was inspired by Bowers & Wilkins and revised from a previous Thingiverse model which is credited.
The sound or acoustic modeling is not what we want to focus on since the original looks like something out of a sci-fi parody. We want to talk about the smart finishing touches that transform a couple of 3D printed shells into enviable centerpieces. The first, and most apparent is the surface. 3D prints from consumer FDM printers are prone to layer lines, and that aesthetic has ceased to be trendy. Textured paint will cover them nicely and requires minimal elbow grease. Besides sand and shells go together naturally. At first glance, the tripod legs holding these speakers seemed like a classy purchase from an upscale furniture store, but they are, in fact, stained wood and ground-down bolts. Nicely done.
The moral is to work smarter, take pictures, then drop us a line.



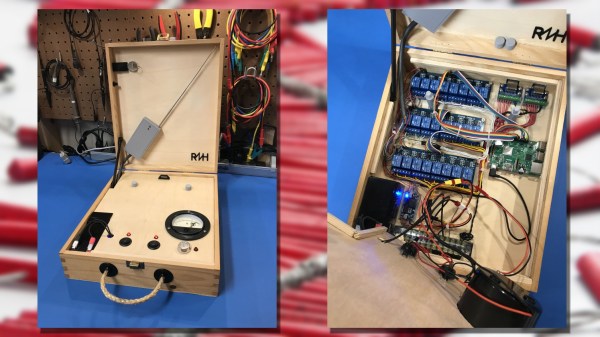
 [netmagi] claims his yearly display is a modest affair, but this controller can address 24 channels, which would be a pretty big show in any neighborhood. Living inside an old wine box is a Raspberry Pi 3B+ and three 8-channel relay boards. Half of the relays are connected directly to breakouts on the end of a long wire that connect to the electric matches used to trigger the fireworks, while the rest of the contacts are connected to a wireless controller. The front panel sports a key switch for safety and a retro analog meter for keeping tabs on the sealed lead-acid battery that powers everything. [netmagi] even set the Pi up with WiFi so he can trigger the show from his phone, letting him watch the wonder unfold overhead. A few test shots are shown in the video below.
[netmagi] claims his yearly display is a modest affair, but this controller can address 24 channels, which would be a pretty big show in any neighborhood. Living inside an old wine box is a Raspberry Pi 3B+ and three 8-channel relay boards. Half of the relays are connected directly to breakouts on the end of a long wire that connect to the electric matches used to trigger the fireworks, while the rest of the contacts are connected to a wireless controller. The front panel sports a key switch for safety and a retro analog meter for keeping tabs on the sealed lead-acid battery that powers everything. [netmagi] even set the Pi up with WiFi so he can trigger the show from his phone, letting him watch the wonder unfold overhead. A few test shots are shown in the video below.