It is interesting to see the wide coverage of a police investigation looking to harvest data from the Amazon Echo, the always-listening home automation device you may know as Alexa. A murder investigation has led them to issue Amazon a warrant to fork over any recordings made during the time of a crime, and Amazon has so far refused.
Not too long ago, this is the sort of news would have been discussed on Hackaday but the rest of my family would have never heard about it. Now we just need to get everyone to think one step beyond this and we’ll be getting somewhere.
What isn’t being discussed here is more of concern to me. How many of you have a piece of tape over your webcam right now? Why did you do that? It’s because we know there are compromised systems that allow attackers to turn on the camera remotely. Don’t we have to assume that this will eventually happen with the Echo as well? Police warrants likely to affect far less users than account breaches like the massive ones we’ve seen with password data.
All of the major voice activated technologies assert that their products are only listening for the trigger words. In this case, police aren’t just looking for a recording of someone saying “Alexa, help I’m being attacked by…” but for any question to Alexa that would put the suspect at the scene of the crime at a specific time. Put yourself in the mind of a black hat. If you could design malware to trigger on the word “Visa” you can probably catch a user giving their credit card number over the phone. This is, of course, a big step beyond the data already stored from normal use of the system.
It’s not surprising that Amazon would be served a warrant for this data. You would expect phone records (although not recordings of the calls) to be reviewed in any murder case. Already disclosed in this case is that a smart water meter from the home reported a rather large water usage during the time of the murder — a piece of evidence that may be used to indicate a crime scene clean-up effort.
What’s newsworthy here is that people who don’t normally think about device security are now wondering what their voice-controlled tech actually hears them say. And this is a step in the right direction.




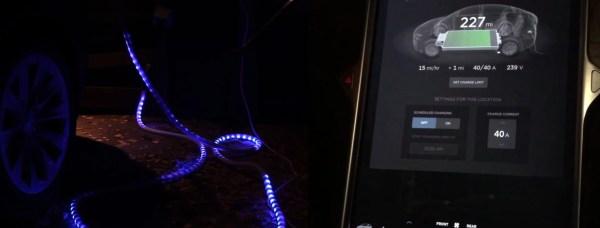
 The basic components behind the build are a current transformer, a NeoPixel LED strip, and an ATtiny44 to run the show. But the quality of the build is where [ch00f]’s project really shines. The writeup is top notch — [ch00f] goes to great lengths showing every detail of the build. The project log covers the challenges of finding appropriate wiring & enclosures for the high power AC build, how to interface the current-sense transformer to the microcontroller, and shares [ch00f]’s techniques for testing the fit of components to ensure the best chance of getting the build right the first time. If you’ve ever gotten a breadboarded prototype humming along sweetly, only to suffer as you try to cram all the pieces into a tiny plastic box, you’ll definitely pick something up here.
The basic components behind the build are a current transformer, a NeoPixel LED strip, and an ATtiny44 to run the show. But the quality of the build is where [ch00f]’s project really shines. The writeup is top notch — [ch00f] goes to great lengths showing every detail of the build. The project log covers the challenges of finding appropriate wiring & enclosures for the high power AC build, how to interface the current-sense transformer to the microcontroller, and shares [ch00f]’s techniques for testing the fit of components to ensure the best chance of getting the build right the first time. If you’ve ever gotten a breadboarded prototype humming along sweetly, only to suffer as you try to cram all the pieces into a tiny plastic box, you’ll definitely pick something up here.