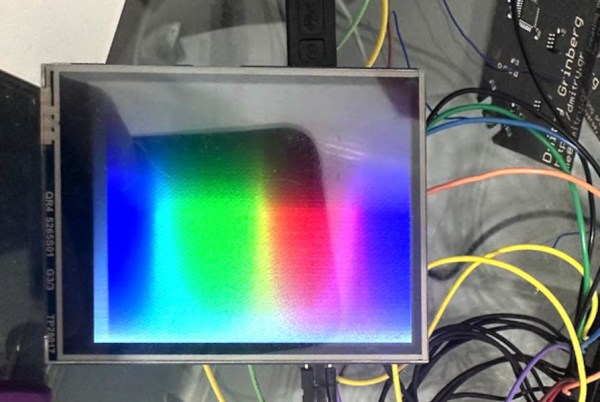
Anyone looking for components for electronics projects, especially robotics, microcontrollers, and IoT devices, has likely heard of Waveshare. They are additionally well-known suppliers of low-cost displays with a wide range of resolutions, sizes, and capabilities, but as [Dmitry Grinberg] found, they’re not all winners. He thought the price on this 2.8-inch display might outweigh its poor design and lack of documentation, and documented his process of bringing it up to a much higher standard with a custom driver for it.
The display is a 320×240 full-color LCD which also has a touchscreen function, but out-of-the-box only provides documentation for sending data to it manually. This makes it slow and, as [Dmitry] puts it, “pure insanity”. His ultimate solution after much poking and prodding was to bit-bang an SPI bus using GPIO on an RP2040 but even this wasn’t as straightforward as it should have been because there are a bunch of other peripherals, like an SD card, which share the bus. Additionally, an interrupt is needed to handle the touchscreen since its default touch system is borderline useless as well, but after everything was neatly stitched together he has a much faster and more versatile driver for this display and is able to fully take advantage of its low price.
For anyone else attracted to the low price of these displays, at least the grunt work is done now if a usable driver is needed to get them up and running. And, if you were curious as to what [Dmitry] is going to use this for, he’s been slowly building up a PalmOS port on hardware he’s assembling himself, and this screen is the perfect size and supports a touch interface. We’ll keep up with that project as it progresses, and for some of [Dmitry]’s other wizardry with esoteric displays make sure to see what he’s done with some inexpensive e-ink displays as well.