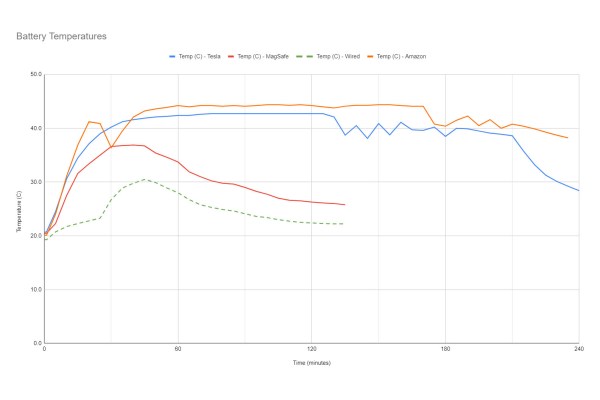
Wireless charging is pretty convenient, as long as the transmitter and receiver speak the same protocol. Just put the device you want to charge on the wireless charger without worrying about plugging in a cable. Yet as it turns out, the disadvantages of wireless charging may be more severe than you think, at least according to tests by iFixIt’s [Shahram Mokhtari] and colleagues. In the article the basics of wireless charging are covered, as well as why wireless charging wastes a lot more power even when not charging, and why it may damage your device’s battery faster than wired charging.
The inefficiency comes mostly from the extra steps needed to create the alternating current (AC) with wireless coupling between the coils, and the conversion back to DC. Yet it is compounded by the issue of misaligned coils, which further introduce inefficiencies. Though various protocols seek to fix this (Qi2 and Apple’s MagSafe) using alignment magnets, these manage to lose 59% of the power drawn from the mains due to these inefficiencies. Wireless chargers also are forced to stay active, polling for a new device to charge, which keeps a MagSafe charger sucking up 0.2 W in standby.
Continue reading “How Wireless Charging Works And Why It’s Terrible”