Love it or hate it, the Nintendo 64 controller doesn’t seem to be going anywhere. Dedicated fans are still looking for ways to use the unique trilobed controller with modern systems, and they won’t be satisfied until they perfectly replicate the original experience. [Shyri Villar] has been working on perfecting a blend of original and modern hardware that looks very promising.
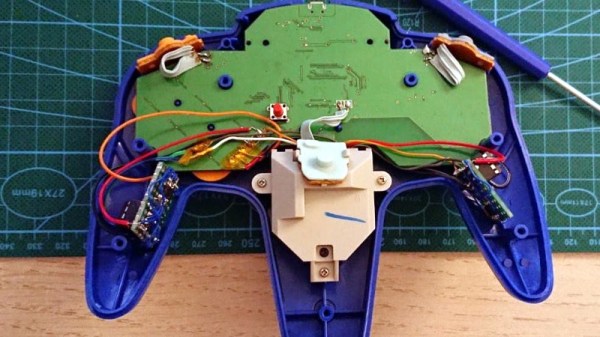
 The project started when [Shyri] found that you could take the internals from a modern third party Bluetooth N64 controller made by 8BitDo and put them into the original controller’s case. This would give you the original buttons back, and overall a more authentic weight and feel. Unfortunately, this usually means dumping the original N64 joystick for the 8BitDo’s.
The project started when [Shyri] found that you could take the internals from a modern third party Bluetooth N64 controller made by 8BitDo and put them into the original controller’s case. This would give you the original buttons back, and overall a more authentic weight and feel. Unfortunately, this usually means dumping the original N64 joystick for the 8BitDo’s.
What [Shyri] wanted to do was install the 8BitDo PCB into an original N64 controller, but adapt Nintendo’s joystick to communicate with it. Unfortunately, since the original joystick used optical encoders and the 8BitDo version uses potentiometers, there’s something of a language gap.
To bridge the divide, both the X and Y dimensions of the joystick get their own PIC12F675 microcontroller and X9C103S digital potentiometer. The microcontrollers read the X and Y values from the original joystick’s encoders, and use the digital potentiometers to provide the 8BitDo with the expected analog input. Right now the electronics are held on two scraps of perfboard tucked into the side “wings” of the controller, but hopefully we’ll see a custom PCB in the future.
If you’re more interested in going back in time with your trusty N64 controller, then you might be interested in learning more about how one hacker managed to hook it up to the MSX.