Most of us know that we should lock our computers when we step away from them. This will prevent any unauthorized users from gaining access to our files. Most companies have some sort of policy in regards to this, and many even automatically lock the screen after a set amount of time with no activity. In some cases, the computers are configured to lock and display a screen saver. In these cases, it may be possible for a local attacker to bypass the lock screen.
[Adrian] explains that the screen saver is configured via a registry key. The key contains the path to a .scr file, which will be played by the Adobe Flash Player when the screen saver is activated. When the victim locks their screen and steps away from the computer, an attacker can swoop in and defeat the lock screen with a few mouse clicks.
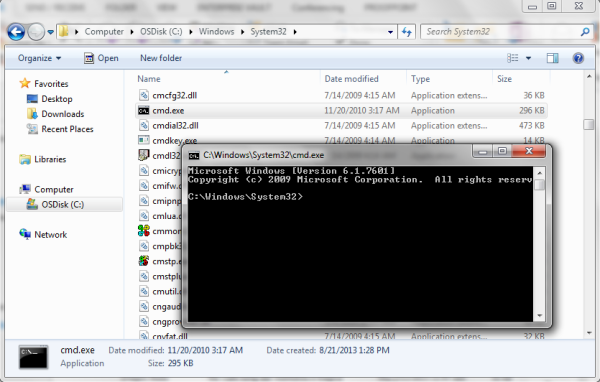
First the attacker will right-click anywhere on the screen. This opens a small menu. The attacker can then choose the “Global settings” menu option. From there, the attacker will click on “Advanced – Trusted Location Settings – Add – Add File”. This opens up the standard windows “Open” dialog that allows you to choose a file. All that is required at this point is to right-click on any folder and choose “Open in a new window”. This causes the folder to be opened in a normal Windows Explorer window, and from there it’s game over. This window can be used to open files and execute programs, all while the screen is still locked.
[Adrian] explains that the only remediation method he knows of is to modify the code in the .swf file to disable the right-click menu. The only other option is to completely disable the flash screen saver. This may be the safest option since the screen saver is most likely unnecessary.
Update: Thanks [Ryan] for pointing out some mistakes in our post. This exploit specifically targets screensavers that are flash-based, compiled into a .exe file, and then renamed with the .scr extension. The OP mentions these are most often used in corporate environments. The exploit doesn’t exist in the stock screensaver.