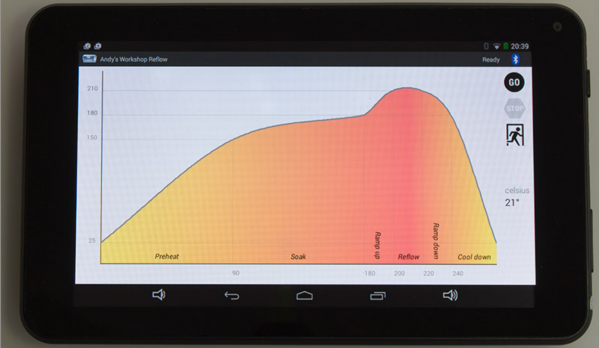
[Andy Brown] is a prolific hacker and ends up building a lot of hardware. About a year back, he built a reflow oven controller. The board he designed used a large number of surface mount parts. This made it seem like a chicken or egg first problem. So he designed a new, easy to build, Android based reflow controller. The new version uses just one, easy to solder surface mount part. By putting in a cheap bluetooth module on the controller, he was able to write an app which could control the oven using any bluetooth enabled Android phone or tablet.
The single PCB is divided into the high voltage, mains powered section separated from the low power control electronics with cutout slots to take care of creepage issues. A BTA312-600B triac is used to switch the oven (load) on and off. The triac is controlled by a MOC3020M optically isolated triac driver, which in turn is driven by a micro controller via a transistor. The beefy 12Amp T0220 package triac is expected to get hot when switching the 1300W load, and [Andy] works through the math to show how he arrived at the heat sink selection. To ensure safety, he uses an isolated, fully encased step down transformer to provide power to the low voltage, control section. One of his requirements was to detect the zero cross over of the mains waveform. Using this signal allows him to turn on the triac for specific angle which can be varied by the micro controller depending on how much current the load requires. The rectified, but unfiltered ac signal is fed to the base of a transistor, which switches every time its base-emitter voltage threshold is reached.
For temperature measurement, [Andy] was using a type-k thermocouple and a Maxim MAX31855 thermocouple to digital converter. This part caused him quite some grief due to a bad production batch, and he found that out via the eevblog forum – eventually sorted out by ordering a replacement. Bluetooth functions are handled by the popular, and cheap, HC-06 module, which allows easy, automatic pairing. He prototyped the code on an ATmega328P, and then transferred it to an ATmega8 after optimising and whittling it down to under 7.5kb using the gcc optimiser. In order to make the board stand-alone, he also added a header for a cheap, Nokia 5110 display and a rotary encoder selector with switch. This allows local control without requiring an Android device.
Gerbers (zip file) for the board are available from his blog, and the ATmega code and Android app from his Github repo. The BoM list on his blog makes it easy to order out all the parts. In the hour long video after the break, [Andy] walks you through solder tip selection, tips for soldering SMD parts, the whole assembly process for the board and a demo. He then wraps it up by connecting the board to his oven, and showing it in action. He still needs to polish his PID tuning and algorithm, so add in your tips in the comments below.
Continue reading “Android-based Reflow Brings Solder Profiles To Your Lab” →



 The specs I’m quoting come from the LG Optimus Exceed 2, which is currently available from Amazon in the USA for $20. The same package has been available for as little as $10 from retail stores in recent weeks. The Exceed 2 is just one of several low-cost Android prepaid phones on the market now, and undoubtedly the list will change. How to keep up with the current deals? We found an unlikely place. Perk farmers. Perk is one of those “We pay you to watch advertisements” companies. We’re sure some people actually watch the ads, but most set up “farms” of drone phones which churn through the videos. The drones earn the farmer points which can be converted to cash. How does this all help us? In order to handle streaming video, Perk farmers want the most powerful phones they can get for the lowest investment. Subreddits like
The specs I’m quoting come from the LG Optimus Exceed 2, which is currently available from Amazon in the USA for $20. The same package has been available for as little as $10 from retail stores in recent weeks. The Exceed 2 is just one of several low-cost Android prepaid phones on the market now, and undoubtedly the list will change. How to keep up with the current deals? We found an unlikely place. Perk farmers. Perk is one of those “We pay you to watch advertisements” companies. We’re sure some people actually watch the ads, but most set up “farms” of drone phones which churn through the videos. The drones earn the farmer points which can be converted to cash. How does this all help us? In order to handle streaming video, Perk farmers want the most powerful phones they can get for the lowest investment. Subreddits like