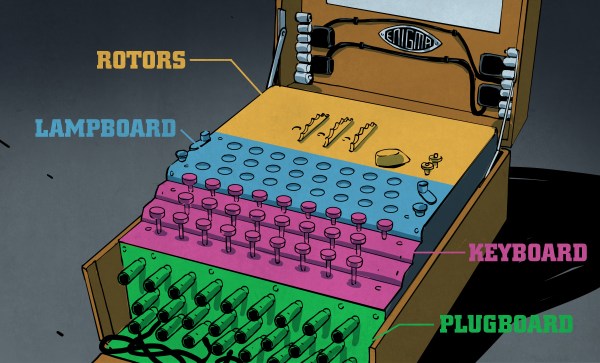
Many smart electric meters in the US use the 900 MHz band to broadcast their usage out to meter readers as they walk the neighborhood. [Jeff Sandberg] used an RTL-SDR dongle and some software to integrate this data into his own home automation system, which lets him keep track of his home’s power usage.
Half of the comment section was appalled that the meters broadcast this data in the clear, and these readers thought this data should be encrypted even if the reach is limited to the home-owner’s front yard. But that would have stopped [Jeff] from accessing his own data as well, and that would be a shame. So there’s clearly a tradeoff in play here.
We see this tradeoff in a lot of hardware devices as well – we want to be able to run our firmware on them, but we don’t want criminals to do the same. We want the smart device to work with the cloud service, but to also work with our own home automation system if we have one. And we want to be able to listen in to our smart meters, but don’t necessarily want others to do so.
The solution here is as easy as it is implausible that it will get implemented. If the smart meters transmitted encrypted, each with their own individual password, then everyone would win. The meter reader would have a database of passwords linked to meter serial numbers or addresses, and the home owner could just read it off of a sticker, optimally placed on each unit. Privacy and usability would be preserved.
This issue isn’t just limited to electric meters. Indeed, think of all of the data that is being sent out from or about you, and what percentage of it is not encrypted and should be, but also about what data is sent out encrypted that you could use access to. The solution is to put you in control of the encryption, by selecting a password or having access to one that’s set for you. Because after all, if it’s your data, it should be your data: private and usable.