A forum post by New Zealand electronics enthusiast [zl2wrw] about retreiving waypoints from a mysterious floppy disk caught our eye. The navigation system on his friend’s fishing boat had died and was replaced. But the old waypoints were stored on a 3-1/2 inch floppy disk that was unreadable on a normal PC. Not to be deterred, [zl2wrw] then looked for another solution — apparently a list of hot NZ fishing spots is worth quite the effort.
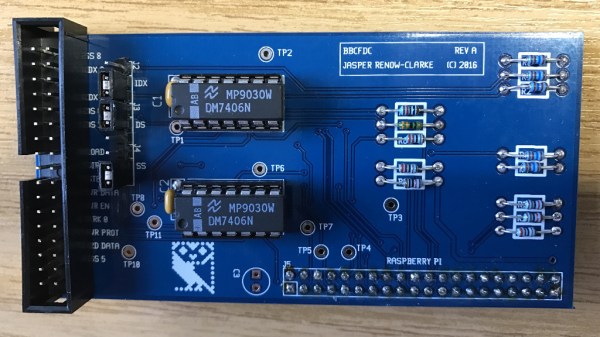
The tool he discovered, and the main point of this story, is the bbc-fdc by [Jasper Renow-Clarke] aka [picosonic]. [Jasper] made this project to read 5-1/4 inch Acorn DFS floppies from his BBC Micro. But bbc-fdc can be used to read a variety of floppy disk formats, such as DOS, C64, Apple II, and others It can also just capture raw magnetic flux transitions on the disk, blissfully unaware of any logical structure to the data. We recently wrote about another Raspberry Pi Floppy Drive Controller project by [Scott Baker]. What sets [picosonic]’s project apart is that he’s not using an FDC controller chip here. The only interface electronics is a couple of open-collector 7406 ICs. Data is read using the SPI peripheral. If you need to archive old floppy disks or do a forensic analysis of unknown disks like [zl2wrw], then one of these two projects will almost certainly do the trick.
Meanwhile back in New Zealand, [zl2wrw] discovered that the floppy format was standard (Modified Frequency Modulation, MFM) by examining the raw flux dump. However, the filesystem was a mystery — it didn’t quite match any of the usual suspects. So [zl2wrw] dug into the hex dump of the data and figured out enough of the structure to manually recover the waypoints. Subsequently, a user on the forum found a document describing the file system used by Furuno GPS units, which proved to be a close match albeit after the fact. Alas, [zl2wrw] hasn’t publish the coordinates of those good fishing spots.
Have you had any successes (or failures) when it comes to reading data from old disks? Or have you encountered peculiar disk formats and/or file systems, where having a tool like this could have been helpful? Let us know in the comments below.