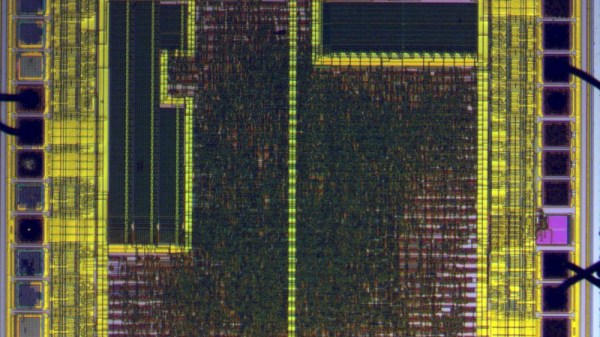
With some free time on his hands waiting for delayed parts to arrive, [Rik] set out to reverse engineer an old VME system he had acquired. VMEbus computers are based on the standard Eurocard PCB format, which defines a wide range of card sizes — the most common being 6U height like [Rik]’s system. They usually consist of a rack-mounted card cage with a passive backplane. Originally, Motorola 68000-based CPU cards were used in VMEbus systems, but any processor could be used as long as you provided the right signals and timings to the system bus. Eurocard systems are less common these days, but are still used in some applications. In fact, if you’re into synthesizers, you may be using Eurocards today — the Eurorack standard is based on the standard 3U card size.
Back to [Rik]’s project, he had no idea what this system was nor how to use it. A bit of probing around and he found two UARTs, a system monitor, and a way to load and dump S-record files. He documents the process quite well, as the internal layout and memory map of the system is unlocked piece by piece. We also like his method of instrumenting the VMEbus signals — logic analyzers are so small today, you can just mount one inside the rack.
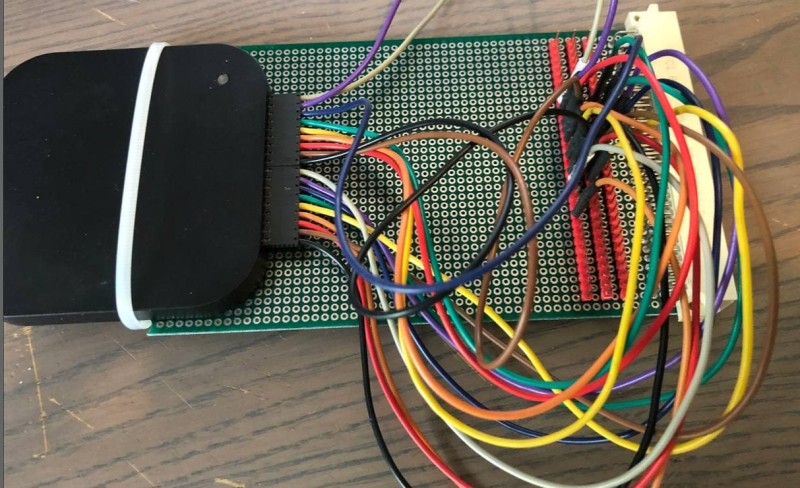
Spoiler alert: [Rik] succeeds in mapping out the memory, writes some small programs in 68k assembly language, and even builds his own LED accessory card so he can blink some lights (as one must do).
We wrote about modularity recently, and VMEbus + Eurocard systems are good examples of modular design. You could quickly put together a robust assembly using entirely off-the-shelf cards, or mix in your own custom cards. But technology advancements in clock speeds and miniaturization have made these card cage, passive backplane systems less and less relevant today. Do any of you still use the VMEbus, or have you designed with them in the past? Let us know down in the comments below.

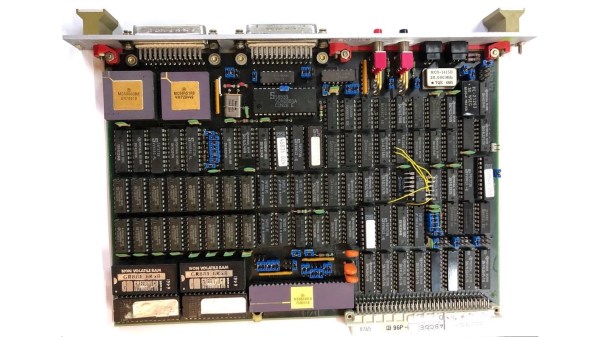
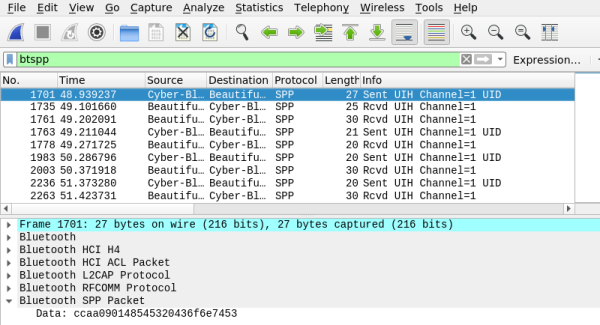




 These questions and more burn within [Hash], a hardware hacker and security researcher who runs the
These questions and more burn within [Hash], a hardware hacker and security researcher who runs the