[Roberto] recently discovered a clever way to gain root access to an HP t520 thin client computer. These computers run HP’s ThinPro operating system. The OS is based on Linux and is basically just a lightweight system designed to boot into a virtual desktop image loaded from a server. [Roberto’s] discovery works on systems that are running in “kiosk mode”.
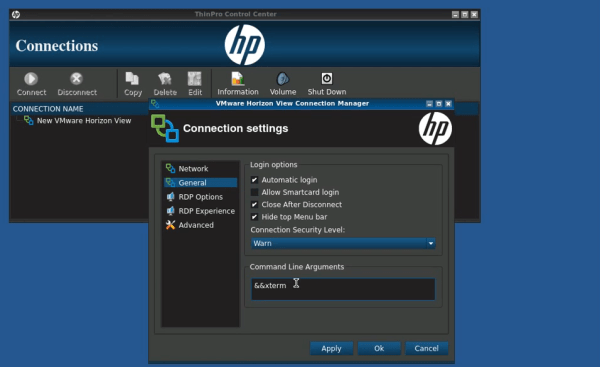
The setup for the attack is incredibly simple. The attacker first stops the virtual desktop image from loading. Then, the connection settings are edited. The host field is filled with garbage, which will prevent the connection from actually working properly. The real trick is in the “command line arguments” field. The attacker simply needs to add the argument “&& xterm”. When the connection is launched, it will first fail and then launch the xterm program. This gives the attacker a command shell running under the context of whichever user the original software is running as.
The next step is to escalate privileges to root. [Roberto] discovered a special command that the default user can run as root using sudo. The “”hpobl” command launches the HP Easy Setup Wizard. Once the wizard is opened, the attacker clicks on the “Thank You” link, which will then load up the HP website in a version of Firefox. The final step is to edit Firefox’s default email program association to xterm. Now when the attacker visits an address like “mailto:test@test.com”, Firefox (running as root) launches xterm with full root privileges. These types of attacks are nothing new, but it’s interesting to see that they still persist even in newer software.