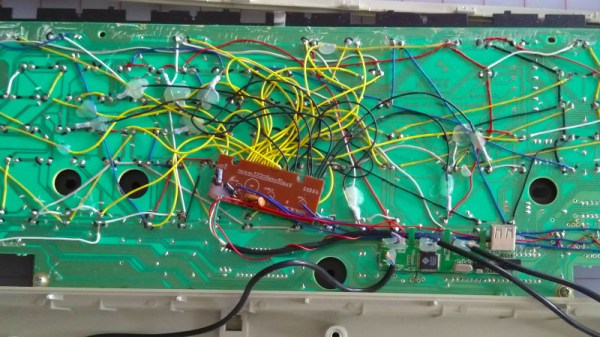
The world of custom keyboards has over the years developed its work into an art form, as mechanical key switches meet USB-HID capable microcontrollers for a plethora of designs as individual as their creators. This was however not always the case, and from the days of 8-bit home computers onwards making a custom keyboard often meant taking a surplus one from elsewhere and adapting its matrix to suit whatever controller interface was at hand. [Julian Calaby]’s USB conversion of an Apple Extended keyboard may be unusual in this day and age and was probably a late example even 15 years ago when he made it, but it remains a glorious piece of bodge-wire hardware hacking at its finest.
The task at hand with this type of conversion is to cut the matrix PCB tracks and replace them with soldered wires to create the new matrix required. This can then be wired to the controller, which in [Julian]’s case came from a cheap USB keyboard. He added a small USB hub to allow for a pair of USB sockets where Apple had put an ADB socket, making for quite a decent older keyboard with an unexpected USB interface.
Now older and wiser, he has plans to revisit his old keyboard with a modern microcontroller board, and needs to revisit the matrix again and give the peripheral new life. We still like the original though, as it captures a moment in time when keyboard matrix hacking made sense, and reminds us of our own youthful hardware follies.
Paging through Hackaday past it’s a testament to the old-school nature of this board that all we can find are microcontroller-based conversions. That’s not to say that cutting up old ‘boards is out of the question though.