Sometimes, we see a project where it’s clear – its creator seriously wants to make a project idea accessible to newcomers; and today’s project is one of these cases. The BYOPM – Bring Your Own Password Manager, a project by [novamostra] – is a Pi Zero-powered device to carry your passwords around in. This project takes the now well-explored USB gadget feature of the Pi Zero, integrates it into a Bitwarden-backed password management toolkit to make a local-network-connected password storage, and makes a tutorial simple enough that anybody can follow it to build their own.
For the physical part, assembly instructions are short and sweet – you only need to solder a single button to fulfill the hardware requirements, and there’s a thin 3D-printable case if you’d like to make the Pi Zero way more pocket-friendly, too! For the software part, the instructions walk you step-by-step through setting up an SD card with a Raspbian image, then installing all the tools and configuring a system with networking exposed over the USB gadget interface. From there, you set up a Bitwarden instance, and optionally learn to connect it to the corresponding browser extensions. Since the device’s goal is password management and storage, it also reminds you to do backups, pointing out specifically the files you’ll want to keep track of.
Overall, such a device helps you carry your passwords with you wherever you need them, you can build this even if your Raspberry Pi skills are minimal so far, and it’s guaranteed to provide you with a feeling that only a self-built pocket gadget with a clear purpose can give you! Looking for something less reliant on networking and more down-to-commandline? Here’s a buttons-and-screen-enabled Pi Zero gadget that uses pass.





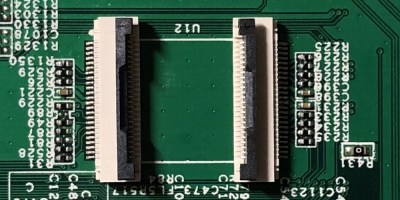
 The metal pads in question seem to be far too thin and structurally unsound, as one can readily spot, their cross-section is dwarfed by the cross-section of cables soldered to them. This would create a segment of increased resistance and heat loss, exacerbated by any flexing of the thick and unwieldy cabling. Due to the metal being so thin, the stress points seem quite flimsy, as one of the metal pads straight up broke off during disassembly of the connector.
The metal pads in question seem to be far too thin and structurally unsound, as one can readily spot, their cross-section is dwarfed by the cross-section of cables soldered to them. This would create a segment of increased resistance and heat loss, exacerbated by any flexing of the thick and unwieldy cabling. Due to the metal being so thin, the stress points seem quite flimsy, as one of the metal pads straight up broke off during disassembly of the connector.
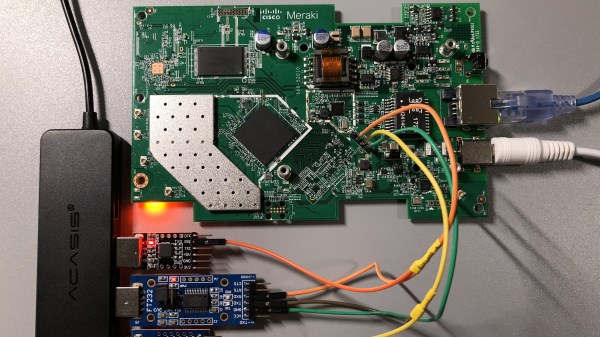
 The flash chip is in TSOP48 package and uses a parallel interface, and an iMX6.LL devboard was used to read, modify and flash back the image — hotswapping the chip, much like we used to do with old parallel-interface BIOS chips. We especially liked the use of FFC cables and connectors for connecting the flash chip to the devboard in a way that allows hotswapping – now that we can see it, the TSOP 0.5 mm pitch and 0.5 mm FFC hardware are a match made in heaven. This hack, of course, will fit many TSOP48-equipped devices, and it’s nice to have a toolkit for it in case you don’t have a programmer handy.
The flash chip is in TSOP48 package and uses a parallel interface, and an iMX6.LL devboard was used to read, modify and flash back the image — hotswapping the chip, much like we used to do with old parallel-interface BIOS chips. We especially liked the use of FFC cables and connectors for connecting the flash chip to the devboard in a way that allows hotswapping – now that we can see it, the TSOP 0.5 mm pitch and 0.5 mm FFC hardware are a match made in heaven. This hack, of course, will fit many TSOP48-equipped devices, and it’s nice to have a toolkit for it in case you don’t have a programmer handy.








