The Sinclair ZX Spectrum was one of the big players in the 8-bit home computing scene of the 1980s, and decades later is sports one of the most active of all the retrocomputing communities. There is a thriving demo scene on the platform, there are new games being released, and there is even new Spectrum hardware coming to market.
One of the most interesting pieces of hardware is the ZX Spectrum Next, a Spectrum motherboard with the original hardware and many enhancements implemented on an FPGA. It has an array of modern interfaces, a megabyte of RAM compared to the 48k of the most common original, and a port allowing the connection of a Raspberry Pi Zero for off-board processing. Coupled with a rather attractive case from the designer of the original Sinclair model, and it has become something of an object of desire. But it’s still an all-in-one a desktop unit like the original, they haven’t made a portable. [Dan Birch has changed all that, with his extremely well designed Spectrum Next laptop.
He started with a beautiful CAD design for a case redolent of the 1990s HP Omnbook style of laptop, but with some Spectrum Next styling cues. This was sent to Shapeways for printing, and came back looking particularly well-built. Into the case went an LCD panel and controller for the Next’s HDMI port, a Raspberry Pi, a USB hub, a USB to PS/2 converter, and a slimline USB keyboard. Unfortunately there does not seem to be a battery included, though we’re sure that with a bit of ingenuity some space could be found for one.
The result is about as good a Spectrum laptop as it might be possible to create, and certainly as good as what might have been made by Sinclair or Amstrad had somehow the 8-bit micro survived into an alternative fantasy version of the 1990s with market conditions to put it into the form factor of a high-end compact laptop. The case design would do any home-made laptop design proud as a basis, we can only urge him to consider releasing some files.
There is a video of the machine in action, which we’ve placed below the break.
Continue reading “Someone’s Made The Laptop Clive Sinclair Never Built”






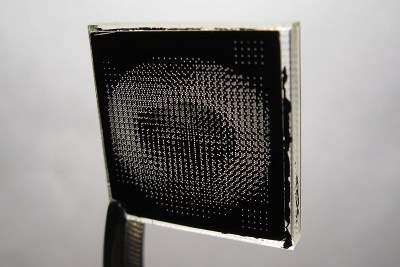
 Ever heard of a sphericular display? [AnubisTTP] laid hands on
Ever heard of a sphericular display? [AnubisTTP] laid hands on