Over the years, Nintendo has had little trouble printing money with their various gaming systems. While they’ve had the odd misstep here and there since the original Nintendo Entertainment System was released in 1983, overall business has been good. But even for the company that essentially brought home video games to the mainstream, this last year has been pretty huge. The release of the Nintendo Switch has rocketed the Japanese gaming giant back into the limelight in a way they haven’t enjoyed in a number of years, and now they’re looking to keep that momentum going into 2018 with a killer new gaming accessory: a cardboard box.

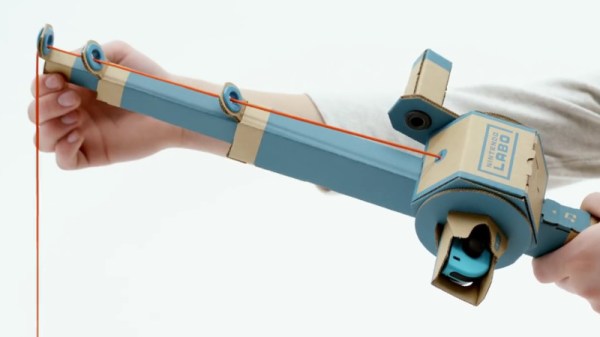
Well, it doesn’t have to be a box, necessarily. But no matter which way you fold it, it’s definitely a piece of cardboard. Maybe a few bits of string here and there. This is the world of “Nintendo Labo”, a recently announced program which promises to let Switch owners create physical objects which they can interact with via specially designed software for the console.
The Labo creations demonstrated in the bombastic announcement video make clever use of the very unique Switch hardware. The removable Joy-Con controllers are generally still used as input devices, albeit in less traditional ways. Twisting and tilting the cardboard creations, which take varied forms such as a fishing rod or motorcycle handlebars, relays input to the appropriate game thanks to the accelerometers and gyroscopes they contain.
Many of the more complex contraptions rely on a less-known feature of the controller: the IR depth camera. By pointing the controller’s camera inside of the devices, the motion of internal components, likely helped along by IR-reflective tape, can be tracked in three dimensions. In the video, the internal construction of some of the devices looks downright intimidating.
Which leads into the natural question: “Who exactly is this for?”
Clearly some of the gadgets, not to mention the folded cardboard construction, are aimed at children, an age group Nintendo has never been ashamed to appeal to. But some of the more advanced devices and overall concept seems like it would play better with creative teens and adults looking to push the Switch in new directions.
Will users be empowered to create their own hardware, and by extension, associated software? Will hackers and makers be able to 3D print new input devices for the Switch using this platform? This is definitely something we’ll be keeping a close eye on as it gets closer to release in April.
The popularity of the Switch has already given rise to a surprising amount of hacking given how new the console is. It will be interesting to see if the introduction of Labo has any effect on the impressive work already being done to bend the console to the owner’s will.